Opsec Is A Capability Of Information Operations
Breaking News Today
Mar 24, 2025 · 6 min read
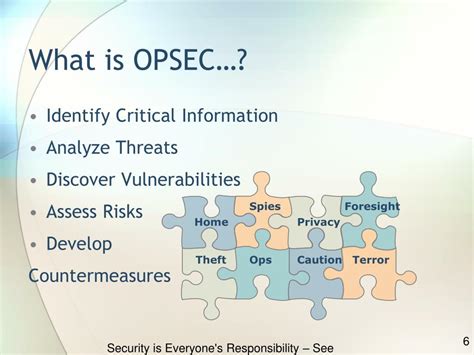
Table of Contents
OPSEC: A Critical Capability of Information Operations
Information operations (IO) are increasingly vital in the modern geopolitical landscape. They encompass the integrated employment of capabilities to affect the perceptions, behaviors, and capabilities of foreign governments, organizations, groups, and individuals. A crucial, often overlooked, component of successful IO is operational security (OPSEC). Without robust OPSEC, even the most meticulously crafted information campaign can be rendered ineffective, or worse, actively detrimental. This article will delve into the multifaceted role of OPSEC as a core capability within the broader context of information operations.
Understanding the Interplay Between OPSEC and Information Operations
Information operations aim to achieve specific objectives by manipulating information flows. These objectives can range from influencing public opinion to disrupting enemy operations. However, the effectiveness of IO hinges on the ability to maintain secrecy and control the narrative. This is where OPSEC comes into play. OPSEC is not merely a security protocol; it's a proactive process focused on identifying, analyzing, and controlling the vulnerabilities that could compromise an IO campaign. It acts as a shield, protecting the delicate mechanisms of influence and manipulation from prying eyes and countermeasures.
Think of IO as a sophisticated chess game. OPSEC is the strategy that ensures your moves remain hidden from your opponent, allowing you to anticipate and counter their responses effectively. Without OPSEC, your opponent can easily predict your moves, anticipate your strategies, and neutralize your efforts.
Key Aspects of OPSEC within IO
Several key aspects of OPSEC are critical for the success of any information operation:
-
Identifying Critical Information: The first step involves systematically identifying all information related to the IO campaign that, if compromised, could jeopardize the operation. This includes details about the campaign's objectives, target audiences, methods, resources, timelines, and personnel involved. Even seemingly insignificant details can become vital pieces of a puzzle for a skilled adversary.
-
Analyzing Vulnerabilities: Once critical information is identified, the next step involves a thorough vulnerability assessment. This process identifies potential avenues through which adversaries could gain access to the sensitive information. This includes assessing vulnerabilities in communication systems, personnel security practices, technology, and physical security.
-
Developing and Implementing Protective Measures: Based on the vulnerability assessment, appropriate protective measures are developed and implemented. This could involve encrypting communications, implementing access controls, using secure communication platforms, employing counterintelligence techniques, and conducting regular security awareness training for personnel.
-
Continuously Monitoring and Adapting: The operational environment is dynamic. Therefore, OPSEC is not a one-time implementation but an ongoing process. Continuous monitoring for new threats and vulnerabilities is vital, alongside the ability to adapt protective measures accordingly. This requires a flexible approach and the ability to respond rapidly to emerging risks.
OPSEC's Role in Different Phases of Information Operations
OPSEC is not just a peripheral concern; it's integral to every phase of an IO campaign. Let's examine its specific role in the different stages:
1. Planning and Preparation: Laying the Foundation for Success
The planning phase is critical. A robust OPSEC plan must be developed alongside the overall IO strategy. This involves identifying potential vulnerabilities from the outset and integrating OPSEC considerations into every aspect of the campaign’s design. Failing to do so can lead to costly mistakes later on. This includes careful consideration of:
- Personnel Security: Thorough background checks and security clearances for all personnel involved are paramount.
- Communication Security: Establishing secure communication channels and protocols is essential to prevent eavesdropping and interception.
- Technology Security: Protecting computer systems and networks from cyberattacks and data breaches is crucial.
2. Execution: Maintaining Secrecy During the Campaign
During the execution phase, maintaining secrecy is paramount. This requires strict adherence to the OPSEC plan and constant vigilance against potential compromises. Continuous monitoring of the information environment is crucial to detect any signs of leaks or attempts to disrupt the operation. Key considerations include:
- Data Handling: Proper handling and storage of sensitive data are critical to prevent accidental leaks or unauthorized access.
- Communication Discipline: Maintaining communication discipline and avoiding the use of unsecure channels is essential.
- Counterintelligence Measures: Implementing counterintelligence measures to identify and neutralize potential threats.
3. Assessment and Evaluation: Learning from Successes and Failures
After the IO campaign is completed, a thorough assessment and evaluation are essential. This involves analyzing the effectiveness of the OPSEC measures implemented and identifying areas for improvement. Lessons learned during this phase inform future campaigns and enhance the overall OPSEC capabilities. Key questions to consider include:
- Were OPSEC measures sufficient? If not, what adjustments are needed?
- Were there any security breaches? If so, what caused them and how can they be prevented in the future?
- How effective was the counterintelligence effort? Were any threats identified and neutralized?
The Human Element in OPSEC: Training and Awareness
The effectiveness of OPSEC heavily relies on the human element. Personnel involved in IO campaigns must be properly trained and educated on OPSEC principles and procedures. This includes understanding the importance of:
- Security Awareness: Developing a strong sense of security awareness and understanding the potential consequences of security breaches.
- Information Handling: Proper handling and storage of classified information.
- Communication Security: Using secure communication channels and protocols.
- Social Engineering Awareness: Recognizing and avoiding social engineering tactics.
- Physical Security: Maintaining physical security and protecting against espionage and sabotage.
Regular security awareness training should be conducted to reinforce these principles and adapt to evolving threats. This training should be tailored to the specific risks faced by the individuals and the nature of the IO campaign. Furthermore, fostering a culture of security within the organization is vital; a collective understanding and commitment to OPSEC are essential for its effectiveness.
OPSEC and the Technological Landscape: Addressing New Challenges
The technological landscape continues to evolve rapidly, presenting both opportunities and challenges for OPSEC. The proliferation of social media, the Internet of Things (IoT), and advanced surveillance technologies necessitates a dynamic and adaptive OPSEC approach. The rise of deepfakes and sophisticated disinformation campaigns pose significant threats that require careful consideration. Key challenges and countermeasures include:
- Cybersecurity: Protecting systems and networks from cyberattacks is increasingly critical. This requires robust cybersecurity measures, including firewalls, intrusion detection systems, and regular security audits.
- Data Privacy: Protecting sensitive data from unauthorized access and misuse is vital. This requires strong data encryption and access control measures.
- Social Media Security: Managing the organization's online presence and mitigating risks associated with social media requires a sophisticated strategy. This includes monitoring social media for potential threats and engaging in proactive counter-narratives.
- Artificial Intelligence (AI): The use of AI for both offensive and defensive purposes requires careful consideration. AI-driven techniques can be used to enhance OPSEC measures, but they can also be used by adversaries to circumvent them.
Conclusion: OPSEC as an Indispensable Component of IO
Operational security is not merely a supporting function within information operations; it's a core capability that underpins the success of the entire endeavor. A robust OPSEC framework, coupled with thorough training and ongoing adaptation to evolving threats, is essential for safeguarding the integrity and effectiveness of IO campaigns. Ignoring OPSEC equates to fighting a war blindfolded, leaving your operations vulnerable to compromise and potentially undermining your strategic objectives. A comprehensive understanding and implementation of OPSEC principles are crucial for anyone involved in information operations in today's complex and challenging global environment. The success of influencing perceptions, shaping narratives, and achieving strategic goals through information operations hinges, decisively, on the unwavering protection provided by a strong OPSEC framework. By integrating OPSEC as a foundational element throughout the entire lifecycle of an IO campaign, organizations can significantly increase their chances of success and minimize the risk of costly failures.
Latest Posts
Latest Posts
-
User Is Unable To Reach Google Com By Typing The Url
Mar 26, 2025
-
How Should A Resident Use A Cane To Aid Ambulation
Mar 26, 2025
-
Moving Average Forecasting Techniques Do The Following
Mar 26, 2025
-
The Enzyme That Accomplishes Transcription Is Termed
Mar 26, 2025
-
Smart Phones And Tablets Are Computers Not Cell Phones
Mar 26, 2025
Related Post
Thank you for visiting our website which covers about Opsec Is A Capability Of Information Operations . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
