What Hostile Intelligence Collection Method Is The Process Of Obtaining
Breaking News Today
Mar 16, 2025 · 5 min read
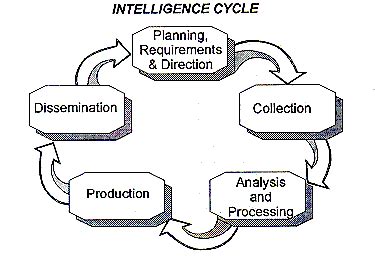
Table of Contents
What Hostile Intelligence Collection Method is the Process of Obtaining Information?
Hostile intelligence collection, also known as espionage or intelligence gathering by adversarial actors, encompasses a wide range of methods employed to surreptitiously obtain sensitive information. Understanding these methods is crucial for individuals and organizations to protect themselves from exploitation and maintain operational security. This article delves into the various techniques used, categorizing them for clarity and providing examples to illustrate their application.
Categorizing Hostile Intelligence Collection Methods
Hostile intelligence collection methods can be broadly categorized into several groups, although there's often significant overlap in practice. These categories aren't mutually exclusive; a single operation may utilize multiple techniques simultaneously.
1. Open Source Intelligence (OSINT) Collection
OSINT involves gathering information from publicly available sources. While seemingly innocuous, skillful manipulation and aggregation of OSINT can yield surprisingly detailed intelligence.
-
Examples: Social media profiles, news articles, company websites, government publications, academic research papers, public records, and even seemingly trivial details gleaned from online forums or blogs.
-
Techniques: Analyzing patterns and inconsistencies in publicly available data, employing advanced search techniques, utilizing social media monitoring tools, and employing data analysis to identify trends and connections.
-
Why it's effective: OSINT is readily accessible, often overlooked, and requires no clandestine operations, making it a low-risk, high-reward method for adversaries.
2. Human Intelligence (HUMINT) Collection
HUMINT focuses on gathering information from people. This involves recruiting and managing human sources, often through manipulation, coercion, or bribery.
-
Examples: Recruiting insiders with access to sensitive information, using deception to elicit information, establishing social engineering campaigns, deploying agents to infiltrate target organizations, and exploiting vulnerabilities in human psychology.
-
Techniques: Developing rapport with potential sources, identifying and exploiting vulnerabilities, utilizing blackmail or bribery, running covert meetings, utilizing dead drops, and employing sophisticated deception techniques.
-
Why it's effective: HUMINT can yield highly valuable and timely information, providing insights unavailable through other methods. However, it's also high-risk, requiring careful planning, security, and management to avoid detection.
3. Signals Intelligence (SIGINT) Collection
SIGINT involves intercepting and analyzing communications, including electronic signals, electromagnetic emissions, and other forms of communication.
-
Examples: Interception of phone calls, emails, text messages, radio transmissions, satellite communications, and data transmitted over networks.
-
Techniques: Utilizing sophisticated electronic surveillance equipment, employing radio frequency analysis, decoding encrypted communications, and employing sophisticated signal processing techniques.
-
Why it's effective: SIGINT can provide real-time insights into communications, plans, and activities, but it requires specialized equipment and expertise, and advancements in encryption can make it increasingly challenging.
4. Imagery Intelligence (IMINT) Collection
IMINT utilizes visual imagery, such as photographs, videos, and satellite imagery, to gather information.
-
Examples: Satellite imagery for mapping infrastructure, aerial photography of military installations, drone surveillance of sensitive areas, and photographic reconnaissance.
-
Techniques: Utilizing high-resolution cameras, employing advanced image processing techniques, conducting aerial reconnaissance missions, and deploying drones for covert surveillance.
-
Why it's effective: IMINT provides visual confirmation of activities and locations, but its effectiveness depends on weather conditions, technological capabilities, and the ability to interpret imagery.
5. Measurement and Signature Intelligence (MASINT) Collection
MASINT uses technical means to collect information about non-communications signals, including electromagnetic, acoustic, and seismic activity.
-
Examples: Detecting nuclear weapon tests through seismic monitoring, analyzing electromagnetic emissions from electronic equipment, identifying acoustic signatures of vehicles or aircraft, and using thermal imaging to detect hidden activities.
-
Techniques: Employing specialized sensors and equipment, utilizing advanced data analysis techniques, and correlating data from multiple sources to create a comprehensive picture.
-
Why it's effective: MASINT offers a unique perspective by identifying patterns and signatures that may not be readily apparent through other means. However, it requires specialized equipment and significant expertise to interpret data.
6. Open Source Intelligence (OSINT) Collection (Revisited in Detail)
Given its prevalence and growing importance, let's examine OSINT collection methods in more detail. Hostile actors leverage OSINT in several ways:
-
Social Media Profiling: Analyzing social media accounts to gather information about individuals' interests, affiliations, locations, and routines. This information can be used to target individuals for recruitment, blackmail, or other malicious activities.
-
Data Aggregation: Combining information from multiple public sources to create a comprehensive profile of an individual or organization. This can be used to identify vulnerabilities and plan attacks.
-
Deep Web and Dark Web Mining: Accessing the hidden parts of the internet to find sensitive information that is not readily accessible through standard search engines. This requires specialized tools and knowledge.
-
Exploiting Public Records: Using publicly available records (property records, court documents, etc.) to gather information about individuals and organizations.
-
Analyzing News and Media: Monitoring news and media outlets to track events, identify trends, and gain insights into the activities of individuals and organizations.
Protecting Yourself from Hostile Intelligence Collection
Protecting yourself and your organization from hostile intelligence collection requires a multi-faceted approach:
-
Security Awareness Training: Educating individuals about the methods used by hostile actors and the importance of protecting sensitive information.
-
Data Security: Implementing strong data security measures to protect sensitive information from unauthorized access. This includes using strong passwords, encryption, access controls, and regular security audits.
-
Physical Security: Implementing physical security measures to protect sensitive areas and equipment from unauthorized access.
-
Communication Security: Using secure communication channels to protect sensitive information from interception. This includes using encryption, virtual private networks (VPNs), and secure messaging applications.
-
Open Source Intelligence Monitoring: Regularly monitor public sources for information about your organization and its employees to identify and address potential vulnerabilities.
-
Threat Intelligence: Staying informed about current threats and tactics used by hostile actors to better prepare for potential attacks.
Conclusion
Hostile intelligence collection is a complex and constantly evolving field. Understanding the methods employed by adversaries is the first step in mitigating the risk of exploitation. By employing a multi-layered security strategy and maintaining a heightened level of awareness, individuals and organizations can significantly reduce their vulnerability to these sophisticated threats. The ongoing arms race between those seeking information and those seeking to protect it necessitates constant vigilance and adaptation. Regular updates on emerging techniques and best practices are critical to maintaining a robust security posture in the face of increasingly sophisticated threats.
Latest Posts
Latest Posts
-
Economists Use The Term Demand To Refer To
Mar 16, 2025
-
Scaffold Are The Workers Qualified To Design Scaffolds
Mar 16, 2025
-
What Conflict Occurs In The Passage Rules Of The Game
Mar 16, 2025
-
Alcohol Can Reduce Your Ability To See What Colors
Mar 16, 2025
-
Coordination Of Balance And Body Movement Is Controlled By The
Mar 16, 2025
Related Post
Thank you for visiting our website which covers about What Hostile Intelligence Collection Method Is The Process Of Obtaining . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
