Which Best Describes The Terrorist Planning Cycle
Breaking News Today
Mar 18, 2025 · 6 min read
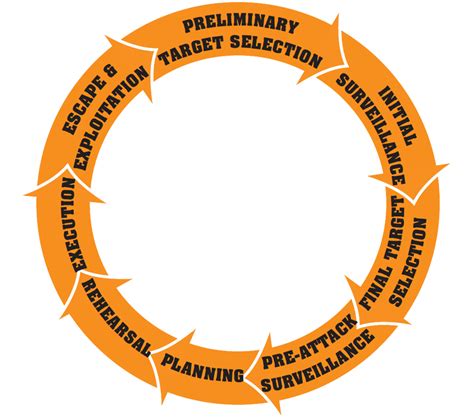
Table of Contents
Which Best Describes the Terrorist Planning Cycle? A Deep Dive into Phases and Mitigation
Terrorism, a global scourge, is a complex phenomenon characterized by premeditated, politically motivated violence perpetrated against non-combatants. Understanding the intricacies of terrorist planning is crucial for effective counterterrorism strategies. This article delves deep into the terrorist planning cycle, exploring its various phases, the actors involved, and the crucial methods for disrupting these lethal operations.
The Stages of Terrorist Planning: A Multifaceted Process
The terrorist planning cycle isn't a monolithic process; rather, it's a dynamic, iterative journey, constantly evolving and adapting to counter-terrorism efforts. While variations exist depending on the group, ideology, and target, a general model encompassing key phases proves useful for analysis and preventative measures. These phases are often overlapping and fluid, but understanding their distinct characteristics is vital.
Phase 1: Target Selection and Surveillance
This initial phase focuses on identifying and assessing potential targets. Terrorists carefully select targets based on several factors:
- Symbolic Value: Targets that hold significant symbolic value for the group (e.g., government buildings, religious sites, media outlets) are often preferred to maximize the impact of the attack.
- Vulnerability: Terrorists seek targets with weak security measures, making them easier to attack with minimal risk. This involves meticulous reconnaissance, often conducted over extended periods.
- Accessibility: The target's accessibility plays a significant role. Ease of approach, escape routes, and the surrounding environment are all carefully considered.
- Impact: The potential impact of the attack is paramount. The expected casualties and the overall damage inflicted are key considerations in target selection.
Surveillance is an integral part of this phase. This can range from simple visual observations to advanced techniques like using drones or employing technological tools for gathering information. The goal is to compile a comprehensive profile of the target, including security protocols, routines, and vulnerabilities. Technological advancements have made surveillance easier and more sophisticated, requiring counter-terrorism efforts to adapt accordingly.
Phase 2: Planning and Preparation
Once a target is selected, the detailed planning phase begins. This involves numerous crucial decisions and preparations:
- Operational Planning: This phase outlines the specific tactics, techniques, and procedures for the attack. This includes selecting the type of weapon, determining the timing of the attack, and establishing communication protocols among team members.
- Resource Acquisition: Terrorist groups acquire the necessary resources, which can include weapons, explosives, vehicles, communications equipment, and funding. This often involves complex networks of suppliers and support systems.
- Team Recruitment and Training: This phase focuses on recruiting and training personnel for the operation. This involves selecting individuals with specific skills and indoctrinating them into the group's ideology. The level of training can vary widely depending on the complexity of the operation.
- Logistics and Support: This encompasses all the logistical aspects, from transportation and communication to escape routes and post-attack plans. The logistical elements are often the most vulnerable points in the cycle, offering potential opportunities for disruption.
Contingency planning is a crucial element of this phase. Terrorist groups anticipate potential problems and develop backup plans in case the primary plan fails. This adaptability makes disrupting their operations even more challenging.
Phase 3: Attack Execution
This is the culmination of the planning process—the actual execution of the attack. The success of this phase hinges on careful coordination, precise timing, and the effective deployment of resources. The operational elements of the attack will directly relate to the previous planning stages and the capabilities of the terrorist group. Some attacks require meticulous precision and synchronized actions, while others might rely on simpler, opportunistic methods.
Following the attack, immediate action plans might be activated by the group, including escape routes and securing their escape after the incident. These operational plans often highlight the group's experience and expertise, underscoring the complex considerations that go into carrying out a successful attack.
Phase 4: Post-Attack Activities
Even after the attack is executed, the cycle doesn't end. The post-attack phase involves several crucial activities:
- Claiming Responsibility: Groups often claim responsibility for their attacks to publicize their cause and sow fear and uncertainty. This serves both propaganda and operational purposes, potentially motivating other recruits and intimidating their intended targets.
- Assessing the Results: This involves evaluating the success of the attack and identifying areas for improvement in future operations. This phase helps them fine-tune their tactics and methods, based on lessons learned.
- Managing Aftermath: This includes dealing with the consequences of the attack, such as managing fallout from law enforcement and public scrutiny. It involves consolidating the narrative and attempting to control the information environment.
This stage often presents an opportunity for law enforcement to gather valuable intelligence through investigations and analysis of the attack's aftermath. The group's actions, both immediate and long-term, provide clues to their organization, capabilities, and future intentions.
Identifying and Disrupting the Terrorist Planning Cycle
Disrupting the terrorist planning cycle is a complex and multifaceted challenge. However, several key strategies can significantly improve effectiveness:
- Intelligence Gathering: Effective intelligence gathering is crucial to identify potential threats and disrupt operations early in the cycle. This involves using human intelligence, signals intelligence, and open-source intelligence to track terrorist activities.
- Law Enforcement Collaboration: Effective counterterrorism requires strong collaboration among law enforcement agencies across different countries and jurisdictions. Information sharing and coordination are critical for effective disruption.
- Community Engagement: Building strong relationships with communities can provide valuable information and early warning signs of potential terrorist activities. This approach relies on trust and fostering partnerships at the local level.
- Border Security: Strengthening border security measures is essential for preventing the flow of weapons, explosives, and personnel across borders. This includes advanced screening technologies and improved inter-agency cooperation.
- Financial Disruption: Cutting off terrorist funding sources is a vital strategy. This involves tracking and freezing terrorist assets, disrupting financial networks, and combating money laundering.
- Counter-Propaganda: Countering terrorist propaganda is crucial to reduce their appeal and influence. This requires a proactive approach to spreading alternative narratives and countering their messages.
- Technological Advancements: Leveraging technology to enhance surveillance, monitor communications, and analyze data can significantly aid in disrupting terrorist operations. This includes utilizing advanced data analytics and artificial intelligence.
The Role of Technology in Modern Terrorist Planning
Technology plays an increasingly significant role in all phases of terrorist planning. From encrypted communication platforms to utilizing social media for propaganda and recruitment, the digital landscape presents both opportunities and challenges for terrorist groups.
Encrypted communication allows them to communicate secretly, hindering law enforcement's ability to intercept their plans. Social media platforms are used for radicalization, recruitment, and disseminating propaganda. Moreover, access to readily available information on bomb-making techniques and other attack methods poses a significant risk.
Counter-terrorism efforts must adapt to these advancements. This includes developing strategies to monitor online activity, decrypt communications, and counteract propaganda effectively. The continuous evolution of technology requires an equally adaptive approach to counterterrorism.
Conclusion: A Continuous Cycle of Adaptation
The terrorist planning cycle is a dynamic process, constantly adapting to counter-terrorism efforts. Understanding its intricacies, from target selection to post-attack activities, is essential for developing effective counter-terrorism strategies. A multi-pronged approach encompassing intelligence gathering, law enforcement collaboration, community engagement, border security, financial disruption, counter-propaganda, and the harnessing of technological advancements is crucial for disrupting this deadly cycle and mitigating the threat of terrorism. The ongoing battle against terrorism necessitates a continuous evolution of counter-terrorism tactics to stay ahead of the ever-changing methods employed by terrorist organizations. The fight is not simply against the immediate threat of a specific attack, but against the ideological underpinnings that fuel the cycle of planning and violence.
Latest Posts
Latest Posts
-
Why Did Many Immigrants Settle In The Cities
Mar 18, 2025
-
Many Of The Progressive Reformers Were
Mar 18, 2025
-
How Is Behavior Therapy Different Than Psychoanalysis
Mar 18, 2025
-
Quien Es El Hijo De Tu Padrastro In English
Mar 18, 2025
-
What Are The Goals Of Using A Disguise
Mar 18, 2025
Related Post
Thank you for visiting our website which covers about Which Best Describes The Terrorist Planning Cycle . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
