Which Of The Following Best Describes Spyware
Breaking News Today
Mar 13, 2025 · 6 min read
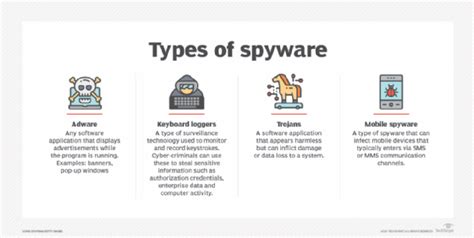
Table of Contents
Which of the Following Best Describes Spyware? A Deep Dive into Invasive Software
Spyware. The word itself evokes a sense of unease, a violation of privacy. But what exactly is spyware? It's more than just a pesky pop-up ad; it's a sophisticated threat that can subtly infiltrate your devices and compromise your sensitive data. This comprehensive guide will delve into the intricacies of spyware, exploring its various forms, detection methods, and effective mitigation strategies. We'll unpack the nuances, separating fact from fiction and empowering you to protect yourself against this insidious threat.
Understanding Spyware: Beyond the Basics
Spyware is malicious software designed to secretly monitor your online activities and gather your personal information without your knowledge or consent. This information can range from seemingly innocuous browsing history to highly sensitive data like banking details, passwords, and even location data. Unlike viruses that primarily aim to disrupt or damage systems, spyware's primary goal is surveillance and data theft. This makes it a particularly insidious threat, as its presence often goes undetected for extended periods.
Key Characteristics of Spyware:
- Stealth: Spyware is designed to operate covertly, making its detection challenging. It often hides itself deep within the operating system, making it difficult to locate and remove.
- Data Harvesting: Its primary function is collecting data. This data can include keystrokes, website visits, login credentials, credit card information, and much more.
- Monitoring: Spyware actively monitors user activity, tracking everything from emails and instant messages to file transfers and online purchases.
- Remote Control: Some advanced spyware allows remote access to the infected device, giving the attacker complete control.
Types of Spyware: A Diverse Threat Landscape
Spyware isn't a monolithic entity. It manifests in various forms, each with its own unique capabilities and targets:
1. Keyloggers: Capturing Every Keystroke
Keyloggers are among the most prevalent types of spyware. These insidious programs record every keystroke made on an infected device, capturing passwords, credit card numbers, and other sensitive information typed into online forms or text editors. They can be hardware-based (physical devices attached to the keyboard) or software-based (installed on the computer). Software keyloggers can be even harder to detect, often masking their presence within legitimate programs or system processes.
2. Screen Captures: Visual Surveillance
Screen capture spyware takes screenshots of the user's screen at regular intervals, providing the attacker with a visual record of their activities. This allows attackers to monitor online banking sessions, observe password entries, or simply track browsing habits. The frequency of captures can vary, from a few snapshots per day to continuous monitoring.
3. Web Bugs and Tracking Cookies: The Invisible Trackers
Web bugs (also known as web beacons) and tracking cookies are small pieces of code embedded in websites. While not always malicious, they can be used to track user browsing habits, collecting data about visited websites, time spent on each page, and clicks on advertisements. While some tracking is legitimate (for analytics and targeted advertising), excessive or unauthorized tracking can be considered spyware.
4. Adware: The Annoying but Potentially Dangerous Cousin
Adware is a form of spyware that displays unwanted advertisements on the user's screen. While generally less intrusive than other types of spyware, adware can slow down system performance, redirect users to malicious websites, and potentially collect data about browsing habits. Some adware bundles itself with free software, making it difficult to avoid during installation.
5. Ransomware (with Spyware Components): A Double Threat
While primarily known for encrypting files and demanding a ransom, some ransomware strains incorporate spyware components. Before encryption, the ransomware may collect sensitive data from the victim's computer, providing the attackers with valuable information even if the ransom is not paid.
6. Remote Access Trojans (RATs): Giving Attackers Full Control
RATs are powerful spyware programs that grant attackers complete remote control over the infected device. This allows them to access files, install additional malware, monitor activity, and even manipulate the system's functions. RATs are particularly dangerous as they can be used for a wide range of malicious activities, from data theft to identity theft.
How Spyware Infects Your Devices: Vectors of Attack
Spyware can infiltrate your devices through several avenues:
- Malicious Downloads: Downloading infected files from untrusted sources, such as torrent websites or file-sharing services.
- Phishing Emails: Clicking on malicious links or attachments in phishing emails disguised as legitimate communications.
- Drive-by Downloads: Visiting compromised websites that automatically download malware without the user's knowledge or consent.
- Software Vulnerabilities: Exploiting security flaws in software to gain access to the system.
- Bundled Software: Installing free software that includes spyware as a hidden component.
Recognizing the Signs of Spyware Infection: Detecting the Intruders
Detecting spyware can be challenging due to its stealthy nature. However, several warning signs can indicate a possible infection:
- Slow System Performance: Spyware can consume significant system resources, leading to slowdowns and sluggish performance.
- Unexplained Pop-up Ads: Excessive or unusual pop-up advertisements can be a sign of adware or other spyware.
- Unusual Network Activity: A consistently high level of network traffic, even when not actively using the internet, may suggest spyware is transmitting data.
- Changes in Browser Settings: Unexplained changes to your browser's homepage, search engine, or other settings can indicate spyware.
- New Programs or Processes: The appearance of unfamiliar programs or processes running in the background can be a sign of spyware.
- Data Loss or Theft: If you suspect sensitive personal information has been compromised, it could be due to a spyware infection.
Combating Spyware: A Multi-Layered Defense Strategy
Protecting yourself from spyware requires a multi-layered approach:
1. Proactive Measures: Prevention is Key
- Keep Software Updated: Regularly update your operating system, antivirus software, and other applications to patch security vulnerabilities.
- Use a Reputable Antivirus Program: A robust antivirus suite is crucial for detecting and removing spyware.
- Be Wary of Downloads: Only download files from trusted sources and avoid suspicious websites.
- Beware of Phishing Emails: Be cautious of emails from unknown senders or those containing suspicious links or attachments.
- Enable Firewall Protection: A firewall can help prevent unauthorized access to your system.
- Use Strong Passwords: Use unique, complex passwords for all your online accounts.
- Enable Two-Factor Authentication: Add an extra layer of security with two-factor authentication whenever possible.
2. Reactive Measures: Removing Spyware
If you suspect a spyware infection, take the following steps:
- Run a Full System Scan: Use your antivirus software to perform a thorough system scan for malware.
- Isolate Infected Devices: Disconnect the infected device from the internet to prevent further data loss.
- Use Specialized Spyware Removal Tools: Some specialized tools are specifically designed to remove stubborn spyware.
- Reinstall Your Operating System (if necessary): In severe cases, reinstalling your operating system may be necessary to completely remove the spyware.
3. Ongoing Vigilance: Staying Ahead of the Curve
- Regularly Monitor System Performance: Keep an eye out for any unusual changes or slowdowns.
- Review Your Browser History and Downloads: Periodically check your browsing history and downloads for suspicious activity.
- Stay Informed About New Threats: Keep up to date on the latest spyware threats and security vulnerabilities.
Conclusion: Protecting Your Digital Privacy
Spyware poses a significant threat to your digital privacy and security. Understanding its various forms, detection methods, and mitigation strategies is crucial for safeguarding your personal information and online activities. By implementing proactive measures and taking immediate action when suspicious activity is detected, you can significantly reduce the risk of spyware infection and protect yourself from its damaging consequences. Remember, vigilance and a layered security approach are essential in the ongoing battle against these insidious threats.
Latest Posts
Latest Posts
-
The Suns Apparent Path Around The Celestial Sphere Is Called
May 09, 2025
-
Most Legal Issues Faced By Counselors Involve
May 09, 2025
-
What Happens In The Stratum Germinativum Milady
May 09, 2025
-
The Manager Is Responsible For Knowing The Food Sanitation Rules
May 09, 2025
-
Which Of The Following Is Not A Neurotransmitter
May 09, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Best Describes Spyware . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.