Which Of The Following Is True About Insider Threats
Breaking News Today
Mar 24, 2025 · 6 min read
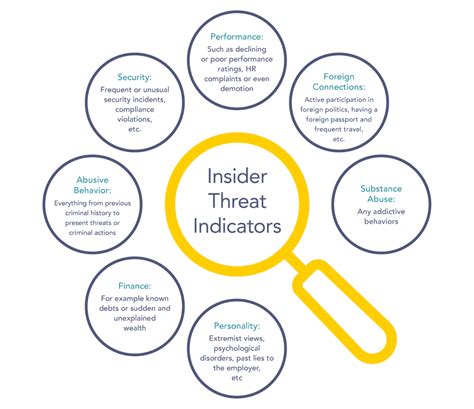
Table of Contents
Which of the Following is True About Insider Threats? A Deep Dive into the Complexities of Internal Risks
Insider threats represent a significant and often overlooked risk to organizations of all sizes. Unlike external attacks that originate from outside the network, insider threats involve individuals with legitimate access who misuse that access to cause harm. This harm can range from simple data breaches to catastrophic financial losses and reputational damage. Understanding the nuances of insider threats is crucial for building robust security strategies. This comprehensive article will delve into the complexities of insider threats, exploring common misconceptions and providing actionable insights to mitigate this pervasive risk.
Defining Insider Threats: More Than Just Malicious Intent
The term "insider threat" is often mistakenly limited to malicious actors. While malicious insiders, those intentionally seeking to cause harm, pose a serious threat, a more accurate definition encompasses a broader range of behaviors. The true scope includes:
-
Malicious Insiders: These individuals actively seek to compromise organizational security, often driven by financial gain, revenge, or ideological motivations. They might steal data, sabotage systems, or plant malware.
-
Negligent Insiders: This group represents a larger and often more insidious threat. They lack malicious intent, but their carelessness or lack of awareness leads to security breaches. Examples include leaving laptops unattended, using weak passwords, or falling prey to phishing scams.
-
Compromised Insiders: In this scenario, an insider's access credentials are stolen or compromised by external attackers, who then use those credentials to gain unauthorized access to sensitive information or systems.
The Spectrum of Harm: Understanding the Impact of Insider Threats
The impact of insider threats can be devastating and far-reaching, affecting various aspects of an organization:
-
Data Breaches: This is perhaps the most common consequence, leading to the loss of sensitive customer information, intellectual property, financial data, and confidential business plans. The repercussions can include hefty fines, legal battles, and reputational damage.
-
Financial Losses: Data breaches and sabotage can lead to direct financial losses through theft, system downtime, and recovery costs. Indirect losses from reputational damage and lost business can be even more significant.
-
Reputational Damage: A major security breach involving an insider can severely damage an organization's reputation, eroding customer trust and potentially impacting future business opportunities.
-
Operational Disruption: Sabotage, malware attacks, or data breaches can severely disrupt an organization's operations, leading to productivity losses and service interruptions.
-
Legal and Regulatory Penalties: Organizations can face significant legal and regulatory penalties for failing to adequately protect sensitive data, especially in regulated industries like healthcare and finance.
Debunking Common Myths About Insider Threats
Several misconceptions surround insider threats, hindering effective prevention and mitigation strategies:
Myth 1: Insider threats are rare and easily detectable.
Reality: Insider threats are surprisingly common and often go undetected for extended periods. Many breaches are not discovered until significant damage has already occurred. The stealthy nature of insider attacks makes them difficult to detect using traditional security measures.
Myth 2: Only disgruntled employees pose a threat.
Reality: As previously discussed, negligent and compromised insiders are equally, if not more, prevalent. Many security breaches stem from unintentional mistakes or compromised accounts, not malicious intent.
Myth 3: Technical solutions alone can effectively mitigate insider threats.
Reality: While technology plays a crucial role, a comprehensive approach requires a multifaceted strategy that integrates technical safeguards with robust policies, procedures, and employee training. Technological solutions can include data loss prevention (DLP) tools, user and entity behavior analytics (UEBA), and security information and event management (SIEM) systems.
Myth 4: Background checks are sufficient to prevent all insider threats.
Reality: Background checks are a valuable tool, but they are not foolproof. They offer a snapshot in time and may not detect evolving risks or changes in an employee's behavior. Ongoing monitoring and assessment are crucial.
Mitigating Insider Threats: A Multi-Layered Approach
Effective insider threat mitigation requires a proactive and layered approach encompassing the following strategies:
1. Strong Security Policies and Procedures:
-
Access Control: Implement the principle of least privilege, granting users only the access required to perform their job duties. Regularly review and update access permissions.
-
Data Classification and Protection: Categorize data based on sensitivity and apply appropriate protection measures, such as encryption and access controls.
-
Data Loss Prevention (DLP): Implement DLP tools to monitor and prevent sensitive data from leaving the organization's control.
-
Security Awareness Training: Regularly train employees on security best practices, including password management, phishing awareness, and safe data handling.
2. Technology-Based Solutions:
-
User and Entity Behavior Analytics (UEBA): UEBA systems analyze user activity patterns to detect anomalies that might indicate malicious or negligent behavior.
-
Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources to identify potential threats.
-
Endpoint Detection and Response (EDR): EDR solutions provide real-time monitoring and response capabilities for endpoints, enabling quick detection and mitigation of insider threats.
-
Data Loss Prevention (DLP): As mentioned above, DLP tools are vital for preventing sensitive data from leaving the organization's control.
3. Human Factors:
-
Background Checks and Vetting: Conduct thorough background checks for all employees, especially those with access to sensitive information.
-
Employee Monitoring: Implement appropriate monitoring practices to detect suspicious activity, but ensure compliance with privacy regulations.
-
Incident Response Plan: Develop a comprehensive incident response plan to effectively handle security breaches, including communication protocols and recovery procedures.
-
Whistleblower Protection: Establish a safe and confidential channel for employees to report suspected security breaches or unethical behavior.
4. Continuous Monitoring and Improvement:
-
Regular Security Audits: Conduct regular security audits to identify vulnerabilities and weaknesses in security controls.
-
Threat Intelligence: Stay informed about emerging threats and adapt security measures accordingly.
-
Performance Evaluation: Include security awareness and compliance as part of performance evaluations.
The Future of Insider Threat Mitigation: AI and Automation
As technology advances, Artificial Intelligence (AI) and machine learning (ML) are playing an increasingly significant role in insider threat detection and mitigation. AI-powered systems can analyze vast amounts of data to identify subtle anomalies that might indicate malicious or negligent behavior. This allows for faster detection and response times, reducing the impact of potential breaches. Automation can streamline many security processes, freeing up security teams to focus on more complex issues.
Conclusion: A Proactive Approach is Essential
Insider threats are a significant and evolving risk that requires a proactive and multifaceted approach. Understanding the nuances of insider threats, debunking common myths, and implementing a comprehensive mitigation strategy are crucial for protecting organizational assets and maintaining a strong security posture. By combining robust security policies, advanced technologies, and a strong focus on employee training and awareness, organizations can significantly reduce their vulnerability to insider threats and safeguard their critical information. Remember, prevention is far more cost-effective than remediation. A continuous cycle of improvement, monitoring, and adaptation is essential in the ever-evolving landscape of cybersecurity threats.
Latest Posts
Latest Posts
-
Rbts Are Responsible For Knowing A Childs Behavior Intervention Plan
Mar 28, 2025
-
Osha Protecting Yourself Against Bloodborne Pathogens Quiz
Mar 28, 2025
-
A Female Infant Is In For A Feeding Consultant
Mar 28, 2025
-
Every Story Has These Three Storytelling Elements What Are They
Mar 28, 2025
-
Which Fact Is True During A Fission Chain Reaction
Mar 28, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Is True About Insider Threats . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
