Are Website Defacement And Dos Possible Cyberattacks Against Websites
Breaking News Today
Mar 14, 2025 · 6 min read
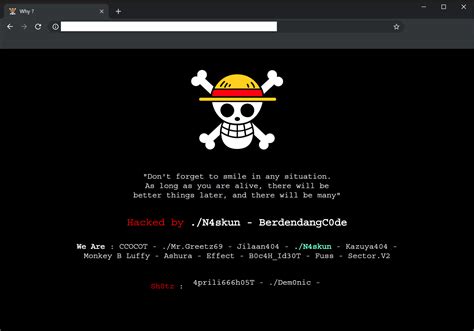
Table of Contents
Are Website Defacement and DDoS Possible Cyberattacks Against Websites?
Yes, website defacement and Distributed Denial-of-Service (DDoS) attacks are both very real and significant threats to websites. They represent two distinct but equally damaging types of cyberattacks, each with its own methods, motivations, and consequences. Understanding their differences and the potential impact is crucial for website owners and administrators to implement effective security measures.
What is Website Defacement?
Website defacement is a type of cyberattack where malicious actors gain unauthorized access to a website's server and alter its content. This can range from minor modifications like changing text and images to completely overhauling the website's appearance with offensive or misleading information. Think of it as digital vandalism – the attacker leaves their mark on the website, often displaying their own messages, logos, or even political statements.
Methods of Website Defacement
Attackers employ various techniques to achieve website defacement, often exploiting vulnerabilities in the website's software, server, or underlying infrastructure. Common methods include:
- Exploiting known vulnerabilities: This involves leveraging publicly known security flaws in Content Management Systems (CMS) like WordPress, Joomla, or Drupal, or other web applications. Outdated or poorly configured software is a prime target.
- SQL injection: This attack technique injects malicious SQL code into website forms or input fields to manipulate the database, granting the attacker control over the website's content.
- Cross-site scripting (XSS): This attack injects malicious scripts into a website, which are then executed by users' browsers. This can allow attackers to steal user data or manipulate the website's content.
- Phishing and social engineering: Tricking website administrators or employees into revealing their credentials, allowing attackers to gain access to the server and deface the website.
- Brute-force attacks: Repeatedly attempting various username and password combinations to gain unauthorized access to the website's control panel or server.
Impact of Website Defacement
The consequences of a website defacement attack can be severe:
- Reputational damage: A defaced website instantly damages the credibility and trustworthiness of the organization or individual behind it. Customers may lose confidence, leading to a decline in business.
- Financial losses: The downtime associated with restoring the website, loss of sales, and the cost of remediation can be significant. Legal fees and potential fines might also be incurred.
- Data breach: While not always the primary goal, defacement can sometimes be a precursor to a larger attack, leading to data theft or other serious breaches.
- Legal implications: Depending on the nature of the defacing content (e.g., illegal or offensive material), legal ramifications can result, including lawsuits and investigations.
What is a Distributed Denial-of-Service (DDoS) Attack?
A DDoS attack is a cyberattack that attempts to overwhelm a website or online service with a flood of internet traffic, rendering it unavailable to legitimate users. Instead of directly attacking the website's content, DDoS attacks target its infrastructure, making it impossible to respond to legitimate requests.
Methods of DDoS Attacks
DDoS attacks utilize a massive number of compromised devices (botnets) to generate the overwhelming traffic. Various attack vectors are used, including:
- Volume-based attacks: These attacks flood the target with massive amounts of data, exceeding its capacity to handle requests. Examples include UDP floods, ICMP floods, and HTTP floods.
- Protocol attacks: These exploit vulnerabilities in specific network protocols to disrupt communication. Examples include SYN floods and TCP floods.
- Application-layer attacks: These target specific applications or services running on the website server, exhausting its resources and causing slowdowns or outages. Examples include HTTP floods and Slowloris attacks.
- Reflection and amplification attacks: These attacks leverage third-party servers to amplify the attack traffic, making them significantly more potent. DNS amplification attacks are a prime example.
Impact of DDoS Attacks
The effects of a DDoS attack are primarily disruptive:
- Website downtime: The primary consequence is the unavailability of the website, preventing users from accessing its services or information.
- Financial losses: Lost revenue, reputational damage, and the cost of mitigation efforts can be substantial.
- Business disruption: The inability to conduct online business transactions or provide services can severely impact an organization's operations.
- Data loss (indirect): While not directly causing data loss, the extended downtime caused by a DDoS attack can lead to indirect data loss if backups aren’t readily available or properly maintained.
- Legal and regulatory repercussions: In certain industries, regulatory compliance mandates uptime and data security, meaning DDoS attacks can trigger legal consequences.
Key Differences Between Website Defacement and DDoS Attacks
While both attacks are harmful, their goals and methods are distinct:
| Feature | Website Defacement | DDoS Attack |
|---|---|---|
| Goal | Alter or destroy website content | Disrupt website availability |
| Method | Exploiting vulnerabilities, injecting code | Flooding with traffic from multiple sources (botnets) |
| Impact | Reputational damage, data breach (potential) | Service disruption, downtime, financial losses |
| Visibility | Immediately apparent (altered website content) | Website becomes inaccessible; may not show malicious code |
| Recovery | Requires restoring website files and security patches | Requires mitigating the attack and restoring service |
Protecting Your Website from Defacement and DDoS Attacks
Both website defacement and DDoS attacks require a multi-layered security approach:
Defacement Prevention:
- Regular software updates: Keep your CMS, plugins, and other software components up-to-date to patch known vulnerabilities.
- Strong passwords and access controls: Use strong, unique passwords for all administrative accounts and implement robust access control measures.
- Input validation and sanitization: Validate all user inputs to prevent SQL injection and XSS attacks.
- Regular security audits and penetration testing: Conduct regular security assessments to identify and address vulnerabilities.
- Web application firewall (WAF): A WAF can help block malicious traffic and protect against common web attacks.
- Security information and event management (SIEM): A SIEM system helps monitor security logs and detect suspicious activity.
DDoS Attack Mitigation:
- Content Delivery Network (CDN): A CDN distributes website traffic across multiple servers, making it more resilient to DDoS attacks.
- Cloud-based DDoS protection: Cloud providers offer DDoS mitigation services that can absorb large volumes of attack traffic.
- Traffic scrubbing: This service filters malicious traffic before it reaches your server.
- Rate limiting: This technique limits the number of requests from a single IP address, preventing simple brute-force attacks.
- Advanced DDoS detection and mitigation tools: These specialized tools can identify and respond to various DDoS attack vectors.
Conclusion: A Proactive Approach is Crucial
Website defacement and DDoS attacks are serious threats that can significantly impact websites. While they are different in their approach, both require a proactive security strategy. Implementing robust security measures, staying updated on the latest threats, and investing in appropriate security tools are essential for protecting your website and minimizing the potential damage from these attacks. Regular backups, disaster recovery planning, and staff training are also vital components of a comprehensive security plan. Ignoring these threats can lead to significant financial and reputational losses. Remember, prevention is always better and cheaper than cure in cybersecurity.
Latest Posts
Latest Posts
-
Which Invention Allowed The Greatest Personal Freedom Of Travel
May 09, 2025
-
Which Event Most Likely Occurs At Point K
May 09, 2025
-
What Does The Time On The Parking Permit Signify
May 09, 2025
-
When Does Decision Making Become More Complex Everfi
May 09, 2025
-
Your Decision To Rent Or Buy Depends On Your
May 09, 2025
Related Post
Thank you for visiting our website which covers about Are Website Defacement And Dos Possible Cyberattacks Against Websites . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.