Based On The Description Provided How Many Insider Threats
Breaking News Today
Mar 17, 2025 · 6 min read
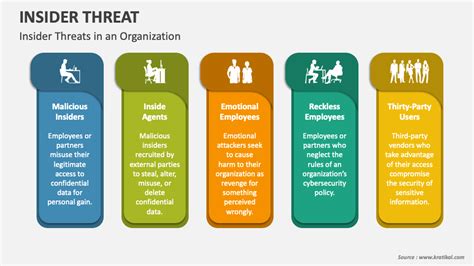
Table of Contents
Decoding Insider Threats: A Deep Dive into Identifying and Mitigating Risks
The chilling reality is that some of the biggest threats to an organization's security don't come from outside hackers, but from within. Insider threats, posed by employees, contractors, or other individuals with legitimate access to an organization's systems and data, represent a significant and often underestimated risk. Determining the exact number of insider threats within a given scenario requires a detailed understanding of the situation. However, we can analyze various scenarios and explore the factors that contribute to the likelihood and severity of these threats. This article delves into the complexities of insider threats, outlining methodologies for identification, the various types of threats, and strategies for mitigation.
Defining the Scope: What Constitutes an Insider Threat?
Before we attempt to quantify insider threats, it's crucial to define what constitutes one. An insider threat isn't simply an employee making a mistake. It involves a deliberate or negligent act by an insider that compromises the confidentiality, integrity, or availability of an organization's assets. This can encompass a wide range of actions, including:
- Data breaches: Deliberate or unintentional release of sensitive information, such as customer data, intellectual property, or financial records.
- Sabotage: Intentional damage to systems, networks, or data, often motivated by malice, revenge, or financial gain.
- Espionage: The theft of intellectual property or sensitive information for the benefit of a competitor or foreign power.
- Fraud: Misuse of organizational resources for personal gain, such as embezzlement or fraudulent expense claims.
- Malicious Insider: An individual intentionally causing harm to the organization.
- Negligent Insider: An individual who unintentionally causes harm due to carelessness or lack of training.
Scenario Analysis: Estimating the Number of Insider Threats
The number of insider threats in any given scenario is highly context-dependent. There's no single answer. To illustrate, let's analyze a few hypothetical scenarios:
Scenario 1: A Small Business with 10 Employees
A small business with 10 employees, employing basic security measures, presents a relatively lower risk of large-scale insider threats. However, the potential still exists. A disgruntled employee might steal client data, or a careless employee could unintentionally expose sensitive information through phishing attacks or weak password practices. In this scenario, the likelihood of a significant number of insider threats is low, perhaps one or two potential incidents over a year, but the impact of those incidents could be substantial given their limited resources and security measures.
Scenario 2: A Large Corporation with 5000 Employees
A large corporation with 5000 employees and sophisticated security systems presents a much more complex picture. The sheer number of employees increases the probability of insider threats. While the sophisticated security infrastructure might detect and mitigate some threats, it's likely that multiple insider threats occur annually, potentially ranging from dozens to hundreds depending on factors like employee vetting, security training, and the effectiveness of monitoring systems. However, many may be detected early or not cause significant damage.
Scenario 3: A Government Agency Handling Classified Information
A government agency handling classified information faces an extremely high risk of insider threats. The consequences of a breach are severe, potentially impacting national security. The number of potential threats here is hard to quantify, but even a single successful insider threat could have catastrophic implications. The focus here would be on preventing any such breaches through rigorous vetting, advanced security measures, and robust monitoring systems. It's less about the number of threats and more about the severity of each individual threat.
Scenario 4: A Healthcare Provider with Access to Patient Data
Healthcare providers dealing with sensitive patient data (PHI) are a prime target for insider threats. The potential for both malicious and negligent breaches is high. Similar to the large corporation, it’s possible to see multiple incidents per year, potentially in the dozens, arising from various sources, including data theft, accidental disclosure, or even the misuse of access privileges.
Factors Influencing the Number of Insider Threats
Several factors influence the number and severity of insider threats:
- Employee Morale and Turnover: High employee turnover and low morale can create a breeding ground for disgruntled employees, potentially leading to malicious insider threats.
- Security Awareness Training: Comprehensive security awareness training can significantly reduce the risk of negligent insider threats by educating employees on best practices and identifying potential risks.
- Access Control Measures: Strong access control measures, including the principle of least privilege, limit the potential damage caused by a compromised account.
- Monitoring and Detection Systems: Real-time monitoring and advanced threat detection systems can help identify and mitigate potential threats early on.
- Background Checks and Vetting: Thorough background checks and vetting processes can help identify potential risks before hiring.
- Data Loss Prevention (DLP) Tools: These tools can monitor and prevent sensitive data from leaving the organization's network.
- Security Culture: A strong security culture, where employees are actively encouraged to report security incidents, is critical in preventing and mitigating insider threats.
Types of Insider Threats and Their Impact
The impact of an insider threat can vary dramatically depending on the type of threat and the sensitivity of the data involved.
1. Malicious Insider: These individuals intentionally cause harm. Their motivations can range from financial gain to revenge or ideological reasons. The impact can be severe, resulting in significant financial losses, reputational damage, and legal repercussions.
2. Negligent Insider: These individuals unintentionally compromise security due to carelessness, lack of training, or failure to follow security protocols. The impact can still be substantial, even if unintentional. A simple mistake, like leaving a laptop unattended, could lead to a data breach.
3. Compromised Insider: An employee whose credentials have been compromised by external actors is a significant threat. This scenario can lead to unauthorized access and data theft. The impact depends on the level of access granted to the compromised account.
Mitigating Insider Threats: A Multi-Layered Approach
Mitigating insider threats requires a multifaceted approach:
- Employee Vetting and Background Checks: This helps identify potentially risky individuals before hiring.
- Comprehensive Security Awareness Training: Regular training should emphasize best practices, phishing awareness, and data security policies.
- Access Control and Privileged Access Management (PAM): Implementing strong access controls, including the principle of least privilege, limits the potential damage from compromised accounts. PAM adds another layer of security to the management of privileged accounts.
- Data Loss Prevention (DLP): These tools help identify and prevent sensitive data from leaving the organization's network.
- User and Entity Behavior Analytics (UEBA): This technology analyzes user behavior patterns to detect anomalies that could indicate malicious activity.
- Regular Security Audits: Regular audits help identify vulnerabilities and weaknesses in security controls.
- Incident Response Plan: A well-defined incident response plan is crucial for quickly containing and mitigating the impact of insider threats.
- Strong Password Policies: Enforce strong, unique passwords and encourage the use of multi-factor authentication.
Conclusion: The Ongoing Battle Against Insider Threats
While it's impossible to provide a single number for the total insider threats faced by an organization without specific details, the examples illustrate the broad range of possibilities. The key takeaway is that the risk of insider threats is real and pervasive, regardless of organizational size or industry. Focusing on proactive measures, such as robust security awareness programs, strong access controls, advanced threat detection systems, and a well-defined security culture, is far more effective than simply trying to count potential threats. It's a continuous battle, requiring ongoing vigilance and adaptation to evolving threats and technologies. By prioritizing prevention and mitigation, organizations can significantly reduce their vulnerability to this insidious threat. The cost of ignoring insider threats far outweighs the cost of implementing comprehensive security measures.
Latest Posts
Latest Posts
-
Describe The Continuous Nature Of The Physical Fitness Concept
Mar 18, 2025
-
High Levels Of Cholesterol Can First Lead Directly To
Mar 18, 2025
-
True Or False Professional And Technical Communication Is Research Oriented
Mar 18, 2025
-
Which Best Describes The Terrorist Planning Cycle
Mar 18, 2025
-
Cdl Combination Test Questions And Answers Pdf
Mar 18, 2025
Related Post
Thank you for visiting our website which covers about Based On The Description Provided How Many Insider Threats . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
