How Do Phishing Simulations Contribute To Enterprise Security
Breaking News Today
Apr 01, 2025 · 6 min read
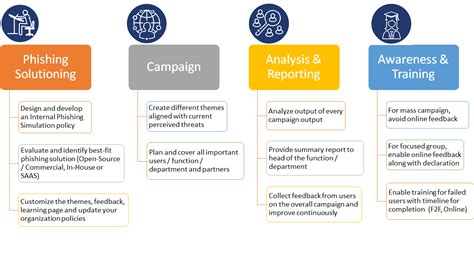
Table of Contents
How Do Phishing Simulations Contribute to Enterprise Security?
Phishing attacks remain a leading cause of data breaches and security incidents for enterprises worldwide. The sophisticated tactics employed by cybercriminals, coupled with the ever-increasing reliance on digital communication, make employees a vulnerable entry point. This is where phishing simulations come into play, acting as a crucial element of a robust enterprise security strategy. They offer a proactive and measurable approach to bolstering employee awareness, improving incident response capabilities, and ultimately, reducing the risk of successful phishing attacks.
Understanding the Role of Phishing Simulations
Phishing simulations are controlled, realistic exercises designed to assess the vulnerability of an organization's employees to phishing attacks. These simulations mimic real-world phishing attempts, exposing employees to deceptive emails, websites, or messages. The goal isn't to trick employees but to gauge their ability to identify and report suspicious activities. By identifying weaknesses in employee awareness and response, organizations can implement targeted training and security measures to significantly reduce their attack surface.
Key Benefits of Implementing Phishing Simulations:
-
Increased Employee Awareness: Perhaps the most significant benefit is the direct improvement in employee awareness of phishing tactics. Through simulated attacks, employees learn to recognize red flags such as suspicious links, grammatical errors, urgent requests, and unexpected attachments. This heightened awareness forms the first line of defense against real-world attacks.
-
Improved Security Posture: Simulations highlight vulnerabilities in existing security protocols and employee behavior. This data allows organizations to strengthen their security posture by implementing more effective security awareness training, updating policies, and enhancing technical safeguards.
-
Measurable Results and ROI: Unlike many security measures, phishing simulations provide tangible, quantifiable results. Organizations can track click-through rates, reporting rates, and overall employee performance, directly demonstrating the return on investment (ROI) of the training program.
-
Enhanced Incident Response: By regularly conducting simulations, employees practice their response protocols in a safe environment. This reduces confusion and hesitation during a real attack, leading to quicker and more effective incident response. Knowing what to do and how to do it in a simulated environment prepares them for actual threats.
-
Compliance and Legal Obligations: Many regulatory frameworks, such as GDPR and HIPAA, mandate robust employee training programs to address cybersecurity risks. Phishing simulations provide demonstrable evidence of compliance, reducing legal and financial liabilities.
Types of Phishing Simulations
Organizations can choose from various types of phishing simulations, each with its own advantages and applications:
1. Targeted Phishing Simulations:
These simulations focus on specific departments, roles, or individuals within the organization. By tailoring the content and delivery method, organizations can assess the vulnerability of high-risk groups and implement targeted training. For example, executives might receive simulations mimicking CEO fraud, while IT staff could encounter more technically sophisticated attacks.
2. Simulated Spear Phishing Attacks:
Spear phishing attacks are highly personalized attacks targeting specific individuals. Simulated spear phishing campaigns mimic these sophisticated attacks, using names, job titles, and other personal information to create highly convincing lures. These simulations are particularly useful in identifying individuals who might be susceptible to highly targeted attacks.
3. Email Phishing Simulations:
The most common type, email phishing simulations involve sending out simulated phishing emails to employees. The emails typically contain malicious links, attachments, or requests for sensitive information. The success rate of these simulations reflects the overall phishing awareness level within the organization.
4. Website Phishing Simulations:
These simulations involve creating fake websites that mimic legitimate websites, such as banking or social media portals. Employees are then directed to these fake websites through emails or other means, testing their ability to identify fraudulent websites and avoid divulging sensitive credentials.
5. SMS/Text Message Phishing Simulations:
With the increasing prevalence of SMS communication, incorporating SMS/text message phishing simulations into the training program is essential. These simulations test employee's ability to recognize fraudulent texts containing malicious links or requests for personal information.
Designing Effective Phishing Simulations
The effectiveness of phishing simulations heavily depends on their design and implementation. Several factors contribute to creating a robust and impactful simulation program:
1. Realistic Scenarios:
The simulations must closely mirror real-world phishing attempts to be effective. This includes using realistic email templates, incorporating relevant social engineering tactics, and leveraging current attack trends.
2. Regular Cadence:
Regular simulations are crucial to maintaining employee awareness and reinforcing lessons learned. A consistent cadence ensures that employees receive ongoing training and remain vigilant against phishing threats.
3. Diverse Attack Vectors:
Utilizing various attack vectors, such as email, SMS, and websites, provides a more comprehensive assessment of employee vulnerability. This ensures that training covers the full spectrum of potential phishing attempts.
4. Post-Simulation Training:
Following the simulation, providing targeted training to those who failed to identify the phishing attempt is critical. This training should focus on the specific weaknesses exposed by the simulation and provide practical strategies for avoiding future attacks.
5. Data Analysis and Reporting:
The data collected from the simulations should be carefully analyzed to identify trends, pinpoint vulnerabilities, and inform future training efforts. Comprehensive reporting helps track the effectiveness of the program and demonstrates the ROI of the investment.
Integrating Phishing Simulations into a Broader Security Strategy
Phishing simulations shouldn't exist in isolation; they should be integrated into a broader security strategy that addresses multiple layers of protection. This includes:
-
Security Awareness Training: Phishing simulations are a key component of comprehensive security awareness training. They provide practical, hands-on experience that complements theoretical lessons.
-
Technical Safeguards: While employee awareness is vital, technical safeguards, such as email filtering, anti-malware software, and multi-factor authentication (MFA), add another layer of protection against phishing attacks.
-
Incident Response Plan: A well-defined incident response plan is essential for mitigating the impact of successful phishing attacks. This plan should outline clear procedures for identifying, containing, and resolving security incidents.
-
Regular Security Audits: Regular security audits help identify vulnerabilities in the organization's security posture and ensure that security measures are up-to-date and effective.
Measuring the Success of Phishing Simulations
Measuring the success of a phishing simulation program involves analyzing various metrics, including:
-
Click-Through Rate: The percentage of employees who clicked on the malicious link or opened the suspicious attachment. A lower click-through rate indicates improved employee awareness.
-
Reporting Rate: The percentage of employees who reported the suspicious email or website. A higher reporting rate indicates a greater understanding of reporting procedures.
-
Time to Report: The time elapsed between receiving the phishing attempt and reporting it. A shorter time to report indicates quicker and more effective incident response.
-
Overall Improvement: Comparing the results of successive simulations reveals the overall improvement in employee awareness and response over time. This provides a clear picture of the program's effectiveness.
Conclusion: A Critical Component of Enterprise Security
Phishing simulations are not simply a "nice-to-have" but a critical component of a robust enterprise security strategy. By providing realistic training, highlighting vulnerabilities, and fostering a culture of security awareness, they significantly reduce the risk of successful phishing attacks. Integrating them into a comprehensive security program, coupled with regular monitoring and analysis, empowers organizations to proactively protect their valuable assets and maintain a secure digital environment. The investment in phishing simulations represents a proactive approach to security, offering demonstrable ROI in terms of reduced risk, improved compliance, and enhanced organizational resilience. By embracing this methodology, enterprises can transform their workforce from a potential point of vulnerability into a formidable line of defense against cyber threats.
Latest Posts
Latest Posts
-
What Are The Two Collisions That Happen In A Crash
Apr 02, 2025
-
A Lucky Individual Won The State Lottery
Apr 02, 2025
-
Correctly Label The Following Anatomical Parts Of A Kidney
Apr 02, 2025
-
Continuously Learning About Your Captivity Environment And The Captor
Apr 02, 2025
-
Cmu Cs Academy Answers Key Unit 3
Apr 02, 2025
Related Post
Thank you for visiting our website which covers about How Do Phishing Simulations Contribute To Enterprise Security . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
