Johan Is A Janitor At A Dod Facility Quizlet
Breaking News Today
Mar 18, 2025 · 5 min read
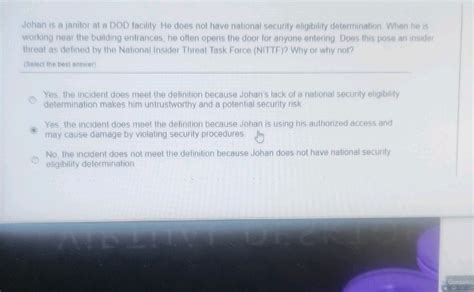
Table of Contents
Johan, the Janitor at a DOD Facility: A Deep Dive into Hypothetical Security Scenarios
This article explores a fictional scenario centered around Johan, a janitor working at a Department of Defense (DOD) facility. We will delve into potential security challenges, focusing on hypothetical situations and analyzing best practices for maintaining a secure environment within such a sensitive location. This isn't a real quizlet question but a thought experiment to highlight important security considerations. We will explore various aspects, from the initial hiring process to potential insider threats and the role of comprehensive training programs.
The Importance of Thorough Background Checks and Vetting
Johan's employment at a DOD facility begins with rigorous screening. Thorough background checks are paramount. This includes but isn't limited to:
- Criminal history checks: A detailed investigation into Johan's past to uncover any criminal convictions, arrests, or pending charges. This is critical in identifying individuals who may pose a risk of theft, espionage, or violence.
- Credit history reviews: While seemingly unrelated, a poor credit history can indicate financial instability, which might motivate an individual to engage in compromising activities.
- Security clearance investigation: A comprehensive assessment of Johan's personal life, including associates, foreign contacts, and financial dealings, to identify potential vulnerabilities to blackmail or coercion. This process can involve interviews with family, friends, and former employers.
- Polygraph testing (where applicable): This controversial method attempts to detect deception. While its accuracy is debated, it can be a part of the vetting process, especially for roles with higher security clearances.
The Importance of Continuous Monitoring: Even after Johan is hired, continuous monitoring is vital. This includes regular reviews of his access badges, work performance, and interactions with personnel and sensitive materials. Any deviation from established norms should trigger an investigation.
Potential Insider Threats and Mitigation Strategies
Johan, like any employee, represents a potential insider threat. While he might not have malicious intent, human error or unintentional compromise can lead to serious consequences. Therefore, a robust security framework must account for these possibilities:
- Accidental data breaches: Johan, while cleaning, might accidentally stumble upon sensitive documents or electronic data. Strict protocols regarding the handling of classified materials, including proper disposal procedures and secure storage, are crucial. Regular security awareness training emphasizing the importance of reporting any unusual findings is essential.
- Phishing and social engineering: Johan could become a victim of phishing attacks, leading to the compromise of his credentials and providing access to restricted areas or data. Training on recognizing and avoiding phishing emails, suspicious links, and social engineering tactics is vital.
- Physical security breaches: Johan's access to the facility and various areas might unintentionally compromise security. For example, inadvertently propping open a door, or failing to properly secure a storage area, could create vulnerabilities that malicious actors can exploit. Reinforced security measures, such as access control systems, surveillance cameras, and motion detectors, are important deterrents. Regular security audits and inspections are equally vital.
- Theft or sabotage: While unlikely, the possibility of Johan stealing sensitive information or equipment, or even sabotaging systems, must be considered. Strong security measures, regular inventory checks, and surveillance systems can mitigate this risk.
The Role of Security Training and Awareness Programs
Comprehensive security awareness training is non-negotiable for all personnel, including Johan. This training should cover various aspects:
- Classification levels and handling procedures: Johan must understand the significance of classified information and the consequences of mishandling such materials.
- Reporting procedures: Clear and accessible channels for reporting suspicious activities or security breaches should be established and communicated effectively. Employees should feel comfortable reporting concerns without fear of retribution.
- Physical security protocols: This includes proper access control procedures, visitor management, and emergency response protocols. Johan should know how to identify and report unauthorized access attempts.
- Cybersecurity awareness: Training on phishing awareness, password security, and safe internet practices is essential to prevent online security breaches.
- Data handling procedures: Proper handling, storage, and disposal of sensitive electronic and physical documents are critical aspects of the training.
- Insider threat awareness: Johan should understand the importance of reporting any suspicious behaviour from colleagues or any actions that could compromise security.
Hypothetical Scenarios and Response Protocols
Let's explore some hypothetical scenarios involving Johan:
Scenario 1: Johan finds a USB drive containing classified information while cleaning.
Johan's immediate response should be to not touch the drive, report the discovery immediately to his supervisor, and avoid any actions that could compromise the integrity of the evidence. The security team would then investigate, secure the drive, and initiate a thorough investigation.
Scenario 2: Johan is approached by a stranger claiming to have lost his security badge and asking for assistance.
Johan should refuse to assist and immediately report the suspicious individual to the security personnel. He should not engage the stranger and should carefully observe their actions, noting any distinguishing features or descriptions.
Scenario 3: Johan observes unusual activity near a restricted area, such as individuals attempting to breach security protocols.
Johan should discreetly observe the activity, note down details such as descriptions of individuals, times, and methods, and immediately report the suspicious activity to the appropriate security personnel using the established channels.
Scenario 4: Johan receives a suspicious email claiming to be from the IT department, requesting his password and other sensitive information.
Johan should not respond to the email and immediately report the suspicious email to the IT department using established reporting procedures. He should never provide his password or any sensitive information via email or other unsecured methods.
Conclusion: Maintaining Security in DOD Facilities
Maintaining security within a DOD facility is a complex and multifaceted endeavor. It requires a holistic approach that integrates robust security measures, thorough background checks, continuous monitoring, comprehensive security training programs, and well-defined response protocols for various potential security breaches. The role of individuals like Johan, even seemingly low-level employees, is critical. Providing comprehensive training and fostering a security-conscious environment are paramount in minimizing risks and mitigating potential threats, ensuring the safety and integrity of national security assets. The hypothetical scenarios explored above highlight the importance of preparedness and a proactive approach to security management. Continuous evaluation and improvement of security protocols are essential to adapt to evolving threats and maintain a secure operational environment. The emphasis on rigorous training, reporting mechanisms, and a culture of security awareness are crucial in mitigating the risks associated with potential insider threats and external attacks.
Latest Posts
Latest Posts
-
The Direct Carry Is Used To Transfer A Patient
Mar 18, 2025
-
The Emancipation Proclamation Of January 1 1863 Quizlet
Mar 18, 2025
-
These Cards Will Get You Drunk Quizlet
Mar 18, 2025
-
Did Quizlet Get Rid Of Q Chat
Mar 18, 2025
-
Myasthenia Gravis Is An Autoimmune Disease In Which Quizlet
Mar 18, 2025
Related Post
Thank you for visiting our website which covers about Johan Is A Janitor At A Dod Facility Quizlet . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
