What Do Virtually All Phishing Emails Have In Common
Breaking News Today
Mar 28, 2025 · 5 min read
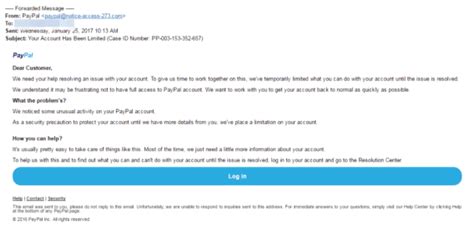
Table of Contents
What Do Virtually All Phishing Emails Have in Common? A Deep Dive into Phishing Tactics
Phishing emails are a persistent and evolving threat, costing individuals and organizations billions annually. While the specifics of each phishing attempt vary—from cleverly crafted narratives to blatant attempts at deception—a surprising number of common characteristics unite them. Understanding these common threads is crucial for developing effective defenses against this pervasive cybercrime. This comprehensive guide delves deep into the shared traits of virtually all phishing emails, equipping you with the knowledge to identify and avoid these dangerous messages.
The Urgency Factor: Creating a Sense of Panic
Perhaps the most pervasive commonality across phishing emails is the creation of urgency. Phishers understand that acting impulsively often overrides critical thinking. They leverage this by employing tactics that pressure recipients into immediate action. This urgency can manifest in several ways:
Time-Sensitive Threats:
- Account suspension/termination notices: These emails claim your account will be suspended or terminated unless you immediately update your information or verify your identity. The implied threat of losing access to vital services—banking, email, social media—is incredibly effective.
- Limited-time offers/promotions: Fake promotions promising incredible discounts or exclusive deals that expire quickly manipulate recipients into clicking links before they supposedly “miss out.”
- Fake invoices with impending late fees: These emails fraudulently claim an overdue invoice needs immediate payment, often threatening legal action or credit rating damage if not paid promptly.
Scarcity and FOMO:
- Limited quantities/availability: Phishing emails often highlight the scarcity of products or services, creating a fear of missing out (FOMO) and prompting hasty clicks.
- Exclusive access/offers: These emails target a sense of exclusivity, suggesting that only a select few recipients have access to a particular offer or opportunity.
Identifying the Urgency Tactic: Always be wary of emails that demand immediate action. Legitimate organizations rarely employ such high-pressure tactics. Take your time to verify the information independently before clicking any links or providing personal details.
The Authority Figure: Impersonation and Social Engineering
Phishing emails almost always attempt to leverage the authority and trustworthiness of a legitimate entity. This is achieved through sophisticated impersonation techniques.
Impersonating Known Brands:
- Fake logos and branding: Phishing emails often mimic the visual identity of well-known brands, including logos, color schemes, and fonts.
- Spoofed email addresses: Phishers use email addresses that closely resemble those of legitimate organizations, often differing only slightly in characters or domain names.
- Name dropping: They might mention names of well-known executives or employees from the organization they're impersonating.
Appealing to Your Trust:
- Leveraging existing relationships: Phishing emails may appear to come from known contacts or friends, using compromised accounts or carefully crafted messages to bypass suspicion.
- Playing on emotions: They frequently evoke emotions like fear, guilt, excitement, or curiosity to influence your behavior. For instance, an email claiming to be from a charity might play on your compassion to elicit donations.
Identifying Impersonation: Always verify the sender's identity independently. Hover over links to check the actual URL before clicking. Contact the organization directly through official channels to confirm the legitimacy of the email. Beware of emails with poor grammar, spelling mistakes, or unprofessional formatting.
The Call to Action: Guiding You Towards a Trap
The ultimate goal of a phishing email is to elicit a specific call to action from the recipient. This action is usually designed to compromise your security.
Common Calls to Action:
- Clicking malicious links: These links often lead to fake login pages or websites designed to steal your credentials.
- Downloading malicious attachments: These attachments can contain viruses, malware, or ransomware that infect your computer.
- Replying with personal information: Phishing emails often request sensitive data like passwords, credit card details, or social security numbers.
- Making a payment: They might direct you to a fake payment website to steal your financial information.
Identifying Malicious Calls to Action: Always be suspicious of emails that ask you to click links, download attachments, or provide personal information. Legitimate organizations will rarely request such details via email.
The Generic Approach: Mass Distribution and Lack of Personalization
While sophisticated phishing campaigns can include some level of personalization, many phishing emails employ a generic approach, targeting a large number of recipients with the same message. This mass distribution is a defining feature.
Lack of Personalization:
- Generic greetings: Instead of using your name, they often use generic greetings like "Dear Customer" or "Valued User."
- Repetitive content: The same message is sent to countless individuals without any customization.
- Unrealistic offers: The offers presented are often too good to be true, targeting a broad audience with a generic appeal.
Identifying Generic Phishing Attempts: The lack of personalization should raise a red flag. Legitimate organizations usually personalize their communications, addressing you by name and tailoring the message to your specific circumstances.
Technical Indicators: Flaws in Design and Origin
Although phishers become more sophisticated, many phishing emails reveal their malicious nature through technical inconsistencies. These are often subtle but important clues.
Poor Grammar and Spelling:
- Typos and grammatical errors: These are common giveaways, indicating a hastily written or poorly translated message.
- Inconsistent branding: Inconsistencies in logos, fonts, or color schemes compared to the legitimate organization's website.
Suspicious Email Addresses and Domains:
- Misspelled domain names: Phishers often use domain names that are very similar to the legitimate organization's domain, but with slight variations.
- Unusual email addresses: The sender's email address might not match the organization's official domain or be from a free email service.
Missing or Inconsistent Security Measures:
- Lack of HTTPS encryption: When hovering over links, verify whether the URL starts with "https://" - a sign of secure transmission.
- Suspicious sender information: Examine the "From" field thoroughly and look for anomalies.
Identifying Technical Indicators: Pay close attention to the details. Poor grammar, spelling mistakes, suspicious email addresses, and unusual formatting are all strong indicators of a phishing attempt.
Staying Ahead of the Phishing Game: Ongoing Vigilance
The tactics employed by phishers are constantly evolving. Staying vigilant and informed is the best defense. Regularly update your security software, be skeptical of unsolicited emails, and report suspicious messages to the appropriate authorities. By understanding the common traits discussed above, you can significantly reduce your vulnerability to phishing attacks and protect yourself from financial loss and identity theft. The combination of technical awareness and critical thinking remains the strongest shield against these persistent threats. Remember: if something seems too good to be true, or too urgent, it probably is.
Latest Posts
Latest Posts
-
Caring For The Surgical Client Ati Quizlet
Mar 31, 2025
-
Education Is Important To Society Because Quizlet
Mar 31, 2025
-
Antibodies Are Produced From Which Cells Quizlet
Mar 31, 2025
-
Ethics And Law In Leadership Edapt Quizlet
Mar 31, 2025
-
Compare And Contrast Indentured Servanthood And Slavery
Mar 31, 2025
Related Post
Thank you for visiting our website which covers about What Do Virtually All Phishing Emails Have In Common . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
