What Does Ip Source Guard Protect Against
Breaking News Today
Mar 26, 2025 · 6 min read
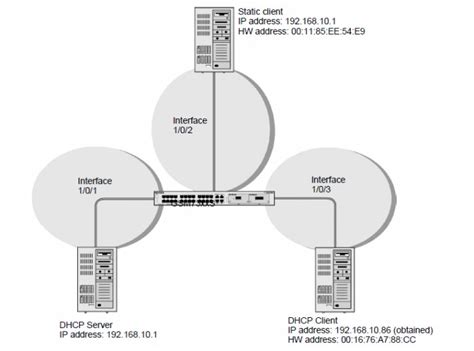
Table of Contents
What Does IP Source Guard Protect Against? A Deep Dive into Network Security
In today's interconnected world, network security is paramount. A single breach can have devastating consequences, leading to data loss, financial damage, and reputational harm. One crucial security measure often deployed to mitigate these risks is IP Source Guard (IPSG). But what exactly does IP Source Guard protect against? This comprehensive guide delves deep into the functionality and benefits of IPSG, exploring its role in bolstering network defenses.
Understanding the Threat Landscape: Why We Need IP Source Guard
Before diving into the specifics of IPSG, it's vital to understand the threats it's designed to combat. Modern networks face a myriad of attacks, but many can be categorized into a few key areas:
1. MAC Spoofing and Address Resolution Protocol (ARP) Spoofing:
- MAC Spoofing: Attackers can alter the Media Access Control (MAC) address of their device, mimicking the address of a legitimate device on the network. This allows them to gain unauthorized access and potentially intercept traffic intended for other devices.
- ARP Spoofing: This attack involves sending false ARP messages to associate a malicious device's MAC address with a legitimate IP address. This allows the attacker to intercept traffic between other devices on the network, acting as a "man-in-the-middle."
2. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks:
While IPSG doesn't directly prevent DoS/DDoS attacks, it can indirectly help by limiting the ability of attackers to flood the network with spoofed traffic originating from internal network addresses.
3. Rogue Devices and Unauthorized Access:
Unauthorized devices, often connected through unsecured ports or vulnerabilities, pose significant risks. These devices can be used to launch attacks, steal data, or simply disrupt network operations. IPSG helps identify and prevent such unauthorized access.
4. Internal Threats:
While often overlooked, insider threats are a significant concern. Malicious or compromised internal users can exploit network vulnerabilities to steal data, disrupt services, or launch attacks against external targets. IPSG can help detect and mitigate some insider threats by identifying devices using unauthorized IP addresses.
How IP Source Guard Works: A Mechanism for Network Protection
IP Source Guard operates by creating a trusted list of devices and their associated MAC addresses and IP addresses. This list is typically configured on network switches and routers. Any device attempting to access the network that isn't on this trusted list will be blocked or flagged.
Here's a breakdown of the key aspects of how IPSG functions:
-
Static Configuration: Administrators manually add approved devices and their corresponding MAC and IP addresses to the IPSG database. This approach offers strong security but requires diligent management, especially in larger networks.
-
Dynamic Learning: Some implementations of IPSG allow for dynamic learning, where the switch automatically learns and adds new devices to the trusted list after they've authenticated successfully. This simplifies management but requires careful consideration of security implications.
-
Port Security: IPSG often works in conjunction with port security features. Port security limits the number of MAC addresses allowed on a specific port, further enhancing protection against MAC address spoofing.
-
Violation Handling: When a device attempts to access the network with an unauthorized IP address or MAC address, IPSG can take various actions, including:
- Blocking the device: This is the most common approach, preventing the unauthorized device from accessing the network entirely.
- Generating an alert: This allows administrators to be notified of potential security breaches, enabling timely intervention.
- Quarantining the device: The device is isolated from the network but not completely blocked, allowing for further investigation.
Benefits of Implementing IP Source Guard
Deploying IP Source Guard offers numerous benefits:
-
Enhanced Security: It significantly reduces the risk of MAC and IP address spoofing, a common technique used in various network attacks.
-
Improved Network Visibility: By monitoring network access attempts, IPSG provides greater visibility into network activity, aiding in the detection of suspicious behavior.
-
Reduced Risk of Unauthorized Access: It prevents rogue devices from connecting to the network, minimizing the chances of unauthorized access and data breaches.
-
Simplified Network Management: While static configuration requires effort, the improved security can simplify management in the long run by reducing the number of security incidents to handle.
-
Compliance: The implementation of IPSG contributes to compliance with various security standards and regulations.
Limitations of IP Source Guard: What IPSG Doesn't Protect Against
While highly effective against certain threats, IP Source Guard has limitations:
-
Doesn't Protect Against All Attacks: IPSG primarily protects against MAC and IP spoofing, and related attacks. It doesn't offer protection against other types of attacks, such as denial-of-service (DoS), SQL injection, or malware infections.
-
Requires Proper Configuration: Misconfiguration or inadequate management of the trusted list can compromise its effectiveness.
-
Can't Prevent All Unauthorized Access: Determined attackers may find ways to bypass IPSG, such as using advanced techniques or exploiting other network vulnerabilities.
-
Dynamic Learning Risks: While simplifying management, dynamic learning features can introduce security risks if not properly configured and monitored.
-
Not a Standalone Solution: IPSG is most effective when used in conjunction with other security measures, such as firewalls, intrusion detection/prevention systems, and robust access control policies.
IP Source Guard vs. Other Security Mechanisms: A Comparative Analysis
IPSG is just one component of a comprehensive network security strategy. It works best when integrated with other security measures:
-
Firewalls: Firewalls filter network traffic based on rules, preventing unauthorized access based on IP addresses, ports, and protocols.
-
Intrusion Detection/Prevention Systems (IDS/IPS): IDS/IPS systems actively monitor network traffic for malicious activity, alerting administrators or automatically blocking suspicious connections.
-
Virtual LANs (VLANs): VLANs segment the network into smaller, isolated broadcast domains, limiting the impact of attacks and improving security.
-
Access Control Lists (ACLs): ACLs restrict network access based on various criteria, including IP addresses, MAC addresses, and ports.
Best Practices for Implementing and Managing IP Source Guard
To maximize the effectiveness of IP Source Guard, follow these best practices:
-
Thorough Planning: Before implementing IPSG, carefully plan the configuration, considering the network topology, device density, and security requirements.
-
Regular Updates: Keep the trusted list up-to-date, adding new devices and removing obsolete ones as needed.
-
Regular Monitoring: Monitor the IPSG logs for any suspicious activity or security breaches.
-
Integration with Other Security Mechanisms: Combine IPSG with other security technologies to create a layered security approach.
-
Security Awareness Training: Educate users about the importance of network security and the risks of unauthorized access.
-
Regular Audits: Conduct regular security audits to evaluate the effectiveness of the IPSG implementation and identify any vulnerabilities.
Conclusion: A Vital Component of Network Security
IP Source Guard is a valuable tool for enhancing network security by protecting against MAC and IP address spoofing and related attacks. However, it's crucial to remember that IPSG is not a silver bullet. It's most effective when used as part of a comprehensive security strategy that includes other security measures, robust security policies, and vigilant monitoring. By understanding its capabilities and limitations, and implementing it correctly, organizations can significantly improve their network's resilience against a range of security threats. Remember to always stay informed about the latest threats and adapt your security strategies accordingly to maintain a strong and secure network environment.
Latest Posts
Latest Posts
-
Dysfunctional Behaviors Are Maladaptive Which Means That They
Mar 29, 2025
-
Choose The Correct Description For Each Phase Of Mitosis
Mar 29, 2025
-
Rn Infection Control And Isolation Assessment 2 0
Mar 29, 2025
-
Continuing Review Of An Approved And Ongoing Study
Mar 29, 2025
-
Simulation Lab 4 1 Module 04 Repair A Duplicate Ip Address
Mar 29, 2025
Related Post
Thank you for visiting our website which covers about What Does Ip Source Guard Protect Against . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
