What Is A Distributed Denial-of-service Attack Quizlet
Breaking News Today
Mar 24, 2025 · 6 min read
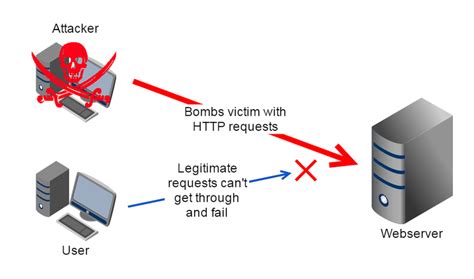
Table of Contents
What is a Distributed Denial-of-Service (DDoS) Attack? A Comprehensive Guide
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. This barrage of requests renders the target service inaccessible to legitimate users. Unlike a traditional Denial-of-Service (DoS) attack, which originates from a single source, a DDoS attack leverages a network of compromised devices, known as a botnet, to launch the assault. This makes them significantly more powerful and harder to defend against. Understanding the intricacies of DDoS attacks is crucial for both individuals and organizations aiming to protect their online presence. This comprehensive guide will delve into the various aspects of DDoS attacks, exploring their mechanics, types, mitigation strategies, and the ever-evolving landscape of this persistent cyber threat.
Understanding the Mechanics of a DDoS Attack
At the heart of a DDoS attack lies the concept of overwhelming a target server or network with an unsustainable volume of traffic. This traffic can take various forms, including:
-
HTTP Flood: This involves flooding the target server with a massive number of HTTP requests, consuming its resources and preventing it from responding to legitimate requests.
-
UDP Flood: Similar to an HTTP flood, but uses UDP (User Datagram Protocol) packets. UDP is connectionless, making it particularly effective for generating large volumes of traffic quickly.
-
SYN Flood: This exploits the TCP three-way handshake process. The attacker sends a large number of SYN requests, but doesn't complete the handshake, leaving the server with incomplete connections and consuming resources.
-
ICMP Flood (Ping of Death): This attack uses ICMP (Internet Control Message Protocol) echo requests (pings) to flood the target.
-
Application Layer Attacks: These attacks target specific applications running on the server, exploiting vulnerabilities to consume resources and disrupt functionality. Examples include HTTP POST floods and Slowloris attacks.
The sheer volume of traffic generated by a botnet makes DDoS attacks incredibly difficult to defend against using traditional methods. The distributed nature of the attack means that blocking individual sources is ineffective, as the attack originates from numerous sources simultaneously.
The Role of the Botnet
The botnet is the backbone of a DDoS attack. This network of compromised computers, servers, and IoT devices (Internet of Things) is controlled by the attacker, often through malware. These compromised devices, known as "bots," are typically unaware of their participation in the attack. The attacker can command the botnet to unleash a coordinated flood of traffic against the target. The size and diversity of the botnet directly impact the severity and effectiveness of the DDoS attack.
Types of DDoS Attacks
DDoS attacks are categorized in several ways, with the most common distinctions being based on the type of traffic used and the target's layer in the network stack:
Based on Traffic Type:
-
Volume-based attacks: These attacks focus on overwhelming the target with sheer volume of traffic, using methods like UDP floods and ICMP floods.
-
Protocol attacks: These attacks exploit vulnerabilities in network protocols like TCP/IP to disrupt services. SYN floods are a prime example.
-
Application layer attacks: These attacks target specific applications running on the server, exploiting vulnerabilities to disrupt their functionality. Examples include HTTP floods and Slowloris attacks.
Based on Target Layer:
-
Network Layer Attacks: These target the network infrastructure itself, overwhelming routers and switches with traffic.
-
Transport Layer Attacks: These target the transport layer protocols (TCP/UDP), disrupting connections between clients and servers.
-
Application Layer Attacks: These are the most sophisticated attacks targeting specific application vulnerabilities to maximize disruption.
Understanding the Impact of DDoS Attacks
The impact of a successful DDoS attack can be devastating:
-
Service Disruption: The primary impact is the complete or partial unavailability of the targeted online service. This can lead to significant financial losses for businesses.
-
Reputational Damage: A DDoS attack can severely damage a company's reputation, eroding customer trust and confidence.
-
Data Loss: While not always a direct consequence, the disruption caused by a DDoS attack can indirectly lead to data loss if backups are inaccessible or systems are compromised.
-
Legal and Regulatory Consequences: Depending on the severity and impact of the attack, companies may face legal and regulatory repercussions.
DDoS Attack Mitigation Strategies
Effectively mitigating DDoS attacks requires a multi-layered approach combining preventive measures, detection systems, and response strategies:
Preventive Measures:
-
Strong Security Posture: Implementing robust security practices, including regular software updates, strong passwords, and firewall configuration, is essential to prevent devices from becoming part of a botnet.
-
Network Segmentation: Isolating critical systems and services from the public internet can limit the impact of an attack.
-
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can block or alert on suspicious patterns.
Detection and Response:
-
DDoS Mitigation Services: These services provide specialized protection against DDoS attacks by absorbing the malicious traffic before it reaches the target. Cloud-based solutions are particularly effective.
-
Traffic Filtering and Rate Limiting: Implementing measures to filter out malicious traffic and limit the rate of incoming requests can help prevent the server from being overwhelmed.
-
Geo-IP Filtering: Blocking traffic from specific geographical locations known for malicious activity can reduce the attack surface.
Advanced Mitigation Techniques
-
Content Delivery Networks (CDNs): CDNs distribute website traffic across multiple servers, making it more resilient to DDoS attacks.
-
Web Application Firewalls (WAFs): These firewalls protect web applications from attacks by filtering malicious requests.
-
Anycast: This technique uses multiple IP addresses pointing to different servers, distributing traffic and making it harder for attackers to overwhelm a single point.
The Evolving Landscape of DDoS Attacks
DDoS attacks are constantly evolving, with attackers employing new techniques and exploiting vulnerabilities to increase the effectiveness of their attacks. Some of the recent trends include:
-
Increased Attack Size and Sophistication: Attacks are becoming larger and more sophisticated, making them harder to mitigate.
-
Use of IoT Devices: The proliferation of IoT devices provides attackers with a vast pool of easily compromised devices to build larger botnets.
-
Targeting of Specific Applications: Attackers are increasingly targeting specific applications and services, rather than just flooding the network.
-
Use of Low-and-Slow Attacks: These attacks use small amounts of traffic over a long period, making them harder to detect and mitigate.
Conclusion
Distributed Denial-of-Service attacks remain a significant threat to online services, demanding a proactive and comprehensive approach to mitigation. Understanding the mechanics, types, and impact of DDoS attacks, coupled with the implementation of robust security measures and mitigation strategies, is crucial for protecting online infrastructure and ensuring the availability of essential services. The constantly evolving nature of these attacks necessitates a continuous vigilance and adaptation to new threats and techniques. Staying informed about the latest trends and best practices is essential for both individuals and organizations striving for a secure online presence in the face of this persistent cyber threat.
Latest Posts
Latest Posts
-
Wall Street Prep Excel Crash Course Exam Answers
Mar 26, 2025
-
Which Level Of Anxiety Enhances The Clients Learning Abilities
Mar 26, 2025
-
A Certifying Officers Certification Attests To The Legality
Mar 26, 2025
-
In Albert Banduras Social Cognitive Theory Behavior Refers To
Mar 26, 2025
-
Which Of The Following Statements Best Describes The Sprint Test
Mar 26, 2025
Related Post
Thank you for visiting our website which covers about What Is A Distributed Denial-of-service Attack Quizlet . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
