Which Of The Following Poses A Security Risk While Teleworking
Breaking News Today
Mar 15, 2025 · 9 min read
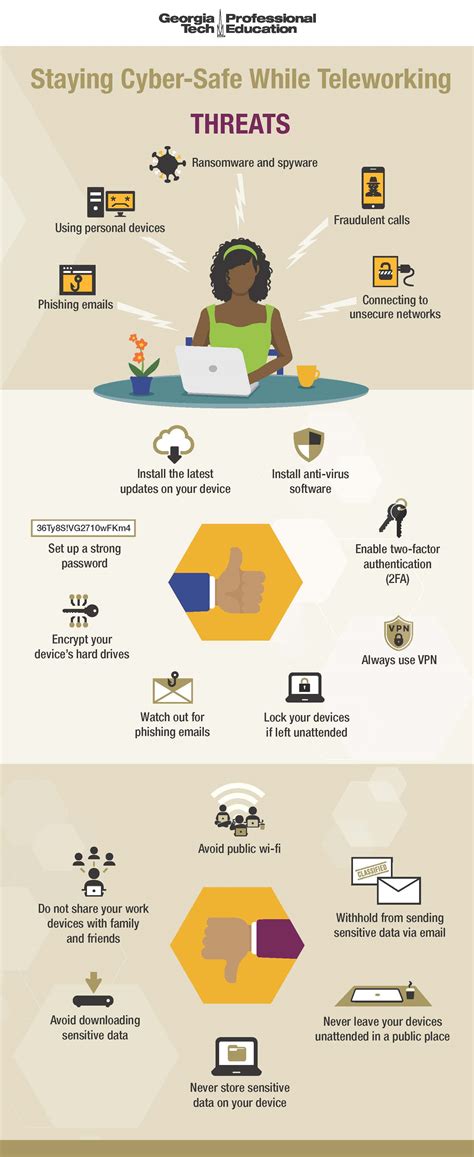
Table of Contents
Which of the Following Poses a Security Risk While Teleworking? A Comprehensive Guide
The rise of teleworking has revolutionized the workplace, offering flexibility and convenience for employees. However, this shift to remote work also presents significant security challenges. Understanding these risks is crucial for both employers and employees to maintain a secure and productive work environment. This comprehensive guide explores various aspects of teleworking security, identifying key vulnerabilities and offering practical solutions.
The Expanding Threat Landscape of Remote Work
The transition to remote work has significantly expanded the attack surface for cybercriminals. No longer confined to a single, secure office network, employees now access company data and systems from diverse and often unpredictable environments. This expands the potential entry points for malicious actors, making security significantly more complex.
1. Unsecured Home Networks: A Major Vulnerability
One of the most significant security risks associated with teleworking is the use of unsecured home networks. Many home Wi-Fi networks lack robust security measures, such as strong passwords, encryption (WPA2/3), and firewalls. This makes them easy targets for hackers who can intercept sensitive data transmitted over the network.
- The Risk: Hackers can easily gain access to your network, potentially stealing company data, installing malware on your devices, or launching further attacks against your employer's network.
- Mitigation Strategies: Use a strong, unique password for your Wi-Fi router. Enable WPA2/3 encryption. Regularly update your router's firmware. Consider using a VPN (Virtual Private Network) to encrypt your internet traffic, even on a secure network.
2. Phishing and Social Engineering Attacks: A Constant Threat
Remote workers are particularly susceptible to phishing and social engineering attacks. These attacks rely on deception to trick individuals into revealing sensitive information, such as passwords, credit card details, or access credentials. With employees working remotely, they are often more isolated and less likely to have immediate access to IT support to verify suspicious emails or messages.
- The Risk: Successful phishing attacks can grant hackers access to company systems, leading to data breaches, financial losses, and reputational damage.
- Mitigation Strategies: Regular security awareness training for employees is crucial. This training should cover identifying phishing emails, recognizing social engineering tactics, and understanding the importance of strong password hygiene. Implementing multi-factor authentication (MFA) significantly reduces the risk of successful phishing attacks.
3. Lack of Physical Security: Protecting Your Workspace
The home environment often lacks the physical security measures present in a traditional office setting. This makes devices and data more vulnerable to theft or unauthorized access. Leaving laptops unattended, failing to lock doors and windows, or not adequately securing sensitive documents are all potential risks.
- The Risk: Physical theft of devices can lead to data breaches and loss of valuable equipment. Unauthorized access to your workspace can compromise sensitive information.
- Mitigation Strategies: Secure your workspace when leaving it, even for short periods. Use strong passwords and encryption to protect your devices. Consider using a laptop lock to secure your device to a desk or other fixed object. Be mindful of where you leave sensitive documents and dispose of them securely.
4. Weak or Reusable Passwords: A Common Weakness
Using weak or easily guessable passwords is a major security vulnerability, regardless of the work environment. However, the distributed nature of remote work makes this risk even more pronounced. Employees working from home may be less likely to adhere to strict password policies or may be tempted to reuse passwords across multiple accounts.
- The Risk: Weak passwords are easily cracked by hackers, granting them access to sensitive company data and systems. Reusing passwords increases the risk of a single compromised password leading to widespread access.
- Mitigation Strategies: Implement and enforce strong password policies, requiring complex passwords with a mix of uppercase and lowercase letters, numbers, and symbols. Encourage the use of password managers to generate and securely store complex passwords. Educate employees on the dangers of password reuse.
5. Unpatched Software and Malware: A Constant Vulnerability
Outdated software and operating systems are prime targets for malware infections. Security vulnerabilities in unpatched software can be exploited by hackers to gain unauthorized access to systems and data. This risk is particularly high for remote workers who may not have access to centralized IT support for timely updates.
- The Risk: Malware infections can lead to data breaches, system crashes, and disruption of business operations.
- Mitigation Strategies: Regularly update software and operating systems on all devices used for work. Use reputable antivirus and anti-malware software and keep it updated. Enable automatic updates whenever possible.
6. Personal Device Use: Balancing Convenience and Security
Many remote workers use personal devices for work purposes, which can pose security risks. Personal devices may not be adequately protected by security software, and they may be more susceptible to malware infections. Mixing personal and work activities on the same device can also lead to accidental data leaks or security breaches.
- The Risk: Personal devices may not meet the security standards required for handling company data. Accidental data leaks or malware infections can compromise sensitive information.
- Mitigation Strategies: Establish clear guidelines for personal device use. Implement mobile device management (MDM) solutions to enforce security policies on personal devices used for work. Separate work and personal data whenever possible, using different devices or separate profiles on a single device.
7. Data Loss and Theft: Protecting Sensitive Information
Data loss and theft are significant risks in any work environment, but they are particularly concerning for remote workers. The distributed nature of remote work makes it harder to track and secure data, increasing the likelihood of loss or theft due to accidental deletion, hardware failure, or malicious attacks.
- The Risk: Data loss can result in financial losses, reputational damage, and legal penalties. Data theft can lead to significant security breaches and compromise sensitive customer or company information.
- Mitigation Strategies: Implement robust data backup and recovery procedures. Use encryption to protect data both in transit and at rest. Educate employees on the importance of data security and responsible data handling practices. Consider using cloud-based storage solutions with strong security features.
8. VPN Misuse and Configuration: A Critical Security Element
Virtual Private Networks (VPNs) are crucial for securing remote worker connections. However, improper configuration or misuse of VPNs can negate their security benefits. Using outdated VPN software, connecting to insecure VPN servers, or using weak VPN credentials can leave remote workers vulnerable to attacks.
- The Risk: An insecure VPN connection can expose sensitive data to interception by hackers. Using a compromised VPN server can lead to complete network compromise.
- Mitigation Strategies: Use reputable VPN providers with strong security protocols. Ensure the VPN software is up to date. Use strong, unique passwords for VPN accounts. Educate employees on the proper use of VPNs and the importance of only connecting to trusted VPN servers.
9. Lack of Centralized Monitoring and Control: Maintaining Visibility
Remote work environments often lack the centralized monitoring and control mechanisms available in traditional office settings. This makes it harder to detect and respond to security incidents in a timely manner. It's crucial to maintain some level of visibility into remote worker activity to ensure security protocols are followed and potential threats are detected early.
- The Risk: Security incidents may go undetected for extended periods, leading to increased damage and potential breaches.
- Mitigation Strategies: Implement security information and event management (SIEM) solutions to monitor remote worker activity. Use endpoint detection and response (EDR) tools to detect and respond to threats on individual devices. Establish clear security protocols and regularly review logs to detect suspicious activity.
10. Insider Threats: The Human Element
Insider threats, stemming from malicious or negligent employees, pose a significant risk in any work environment, including remote settings. Remote work can exacerbate this risk due to the increased difficulty in monitoring employee behavior and enforcing security policies.
- The Risk: Malicious insiders can steal data, sabotage systems, or leak sensitive information. Negligent insiders can inadvertently expose sensitive data due to a lack of awareness or training.
- Mitigation Strategies: Conduct thorough background checks on employees. Implement robust access control policies, granting employees only the necessary access privileges. Provide regular security awareness training to educate employees on the risks of insider threats. Monitor employee activity and access logs for suspicious behavior.
Strengthening Telework Security: Practical Steps
Addressing the security risks associated with teleworking requires a multi-faceted approach involving technological solutions, security policies, and employee training.
Implementing Robust Security Policies
- Develop a comprehensive remote work security policy: This policy should clearly outline acceptable use of company devices and networks, data security protocols, and password management guidelines.
- Enforce strong password policies: Require complex passwords, regular password changes, and multi-factor authentication (MFA).
- Implement access control measures: Grant employees only the minimum necessary access to systems and data.
- Regularly update software and operating systems: Ensure that all devices used for work are kept up-to-date with the latest security patches.
- Use strong encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
- Conduct regular security awareness training: Educate employees on the risks associated with teleworking and best practices for maintaining security.
Utilizing Technological Solutions
- Employ VPNs: Mandate the use of VPNs for all remote workers to encrypt their internet traffic and protect their connections.
- Implement endpoint detection and response (EDR) solutions: These tools can monitor employee devices for malware and other threats.
- Use security information and event management (SIEM) systems: SIEM systems can centralize security logs and provide valuable insights into potential threats.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security, making it more difficult for hackers to gain unauthorized access.
- Utilize cloud-based security solutions: Cloud-based security solutions can provide centralized management and monitoring of security controls.
Fostering a Security-Conscious Culture
- Promote a culture of security awareness: Encourage employees to report suspicious activity and ask questions if they are unsure about security practices.
- Provide regular security updates and training: Keep employees informed about the latest security threats and best practices.
- Establish clear communication channels: Ensure that employees have a clear method of reporting security incidents or seeking assistance.
- Conduct regular security audits: Assess the effectiveness of security measures and identify areas for improvement.
By adopting a comprehensive approach that combines strong security policies, effective technological solutions, and a security-conscious culture, organizations can mitigate the security risks associated with teleworking and maintain a secure and productive remote workforce. Remember, security is an ongoing process, not a one-time fix. Regularly review and update your security measures to adapt to the ever-evolving threat landscape.
Latest Posts
Latest Posts
-
Which Of The Following Is True Of A Qualified Plan
Mar 15, 2025
-
The Democratic Party Of The 1920s Was
Mar 15, 2025
-
What Is The First Step In Reading Dramatic Dialogue
Mar 15, 2025
-
A Rapid Irregular Pulse Following Blunt Trauma
Mar 15, 2025
-
Growing Recognition That Work And Are Interwoven
Mar 15, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Poses A Security Risk While Teleworking . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
