Identifying And Safeguarding Personally Identifiable Information Quizlet
Breaking News Today
Mar 23, 2025 · 5 min read
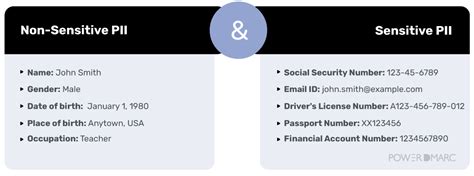
Table of Contents
Identifying and Safeguarding Personally Identifiable Information: A Comprehensive Guide
Personally Identifiable Information (PII) is data that can be used to identify an individual. Protecting this information is crucial for both individuals and organizations. This comprehensive guide will delve into the intricacies of identifying and safeguarding PII, offering practical strategies and insights. We'll explore various types of PII, the risks associated with its exposure, and effective methods for prevention and remediation.
What is Personally Identifiable Information (PII)?
PII encompasses any data that can be used on its own or with other information to identify, contact, or locate a single person. It's far broader than simply a name and address. Let's examine some key categories:
Categories of Personally Identifiable Information:
-
Direct Identifiers: These directly identify an individual. Examples include:
- Full Name: First, middle, and last names.
- Social Security Number (SSN): A unique identifier used in many countries.
- Driver's License Number: Unique to each driver.
- Medical Record Number: Used to track medical history.
- Biometric Data: Fingerprints, facial recognition data, DNA.
- Passport Number: Unique identifier for international travel.
- Email Address: Can be linked to an individual.
- Phone Number: Connects directly to a person.
- Financial Account Numbers: Credit card numbers, bank account numbers, etc.
- Location Data: GPS coordinates, IP addresses.
-
Indirect Identifiers: These, when combined with other information, can be used to identify an individual. Examples include:
- Date of Birth: Combined with other information, it can uniquely identify someone.
- Place of Birth: Provides additional context for identification.
- Mother's Maiden Name: Often used as a security question.
- Employment History: Can narrow down the pool of potential individuals.
- Education History: Similarly, helps in identifying someone.
- Online Usernames/Handles: Especially if consistent across multiple platforms.
The Risks of PII Exposure
The unauthorized disclosure of PII can have severe consequences. These risks include:
Identity Theft and Fraud:
This is perhaps the most significant threat. With sufficient PII, criminals can open fraudulent accounts, apply for loans, file taxes, or even assume someone's identity entirely. The financial and emotional toll of identity theft can be devastating.
Financial Loss:
Access to financial account information can lead to direct financial losses through unauthorized transactions, bank account drainages, and credit card fraud. Recovering from such losses can be a protracted and difficult process.
Reputation Damage:
The misuse of PII can damage an individual's reputation, particularly if the information is used for malicious purposes like spreading false information or engaging in online harassment.
Legal and Regulatory Penalties:
Organizations that fail to adequately protect PII can face significant fines and legal repercussions. Data breach notification laws in many jurisdictions require companies to disclose breaches to affected individuals and regulatory bodies.
Emotional Distress:
The experience of having one's PII exposed can cause significant emotional distress, anxiety, and feelings of violation and helplessness. The psychological impact should not be underestimated.
Safeguarding Personally Identifiable Information: Best Practices
Implementing robust security measures is vital to protect PII. These measures can be categorized into preventative and reactive strategies.
Preventative Measures:
-
Data Minimization: Only collect the PII absolutely necessary for the intended purpose. Avoid collecting unnecessary information.
-
Data Security: Implement strong security measures to protect PII from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes:
- Access Control: Restrict access to PII based on the principle of least privilege. Only authorized personnel should have access to sensitive information.
- Encryption: Encrypt PII both in transit and at rest. Encryption renders data unreadable without the decryption key.
- Strong Passwords and Authentication: Enforce strong password policies and implement multi-factor authentication (MFA) to enhance security.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure compliance with security standards.
- Firewall Protection: Use firewalls to block unauthorized access to networks and systems.
- Intrusion Detection/Prevention Systems: Monitor network traffic for suspicious activity.
- Data Loss Prevention (DLP) Tools: Prevent sensitive data from leaving the organization's control.
-
Employee Training: Educate employees about the importance of PII protection and provide training on security best practices.
-
Physical Security: Secure physical access to areas where PII is stored or processed.
-
Vendor Management: Conduct due diligence on vendors who handle PII to ensure they have adequate security measures in place.
-
Data Backup and Recovery: Implement robust backup and recovery procedures to ensure business continuity in case of a data breach.
-
Regular Software Updates: Keep all software and systems updated with the latest security patches.
-
Privacy Policy: Clearly articulate your organization's privacy policy and data handling practices.
Reactive Measures:
-
Incident Response Plan: Develop and regularly test an incident response plan to address data breaches effectively.
-
Data Breach Notification: Comply with all applicable data breach notification laws.
-
Forensic Investigation: Conduct thorough forensic investigations to determine the cause of a data breach and identify any compromised information.
-
Remediation: Implement measures to remediate the breach and prevent future incidents.
Specific Examples of Safeguarding PII
Let’s examine some practical examples in different contexts:
Healthcare:
-
HIPAA Compliance: Healthcare organizations must comply with the Health Insurance Portability and Accountability Act (HIPAA) to protect patient health information (PHI), a specific type of PII. This includes encryption, access controls, and employee training.
-
Data Masking: Replacing sensitive data elements with non-sensitive substitutes for testing and development purposes.
Financial Institutions:
-
PCI DSS Compliance: Financial institutions that process credit card payments must comply with the Payment Card Industry Data Security Standard (PCI DSS), a stringent security standard designed to protect cardholder data.
-
Fraud Detection Systems: Implementing systems to detect and prevent fraudulent transactions.
Educational Institutions:
- FERPA Compliance: Educational institutions must comply with the Family Educational Rights and Privacy Act (FERPA) to protect student educational records. This involves maintaining student data security and controlling access.
Government Agencies:
- Compliance with relevant laws and regulations: Government agencies often handle highly sensitive PII and must adhere to strict regulations regarding its storage, processing, and access.
Conclusion: A Proactive Approach to PII Protection
Protecting PII is not a one-time task, but an ongoing process requiring vigilance and proactive measures. By understanding the risks associated with PII exposure and implementing robust security protocols, both individuals and organizations can significantly reduce their vulnerability. Continuous monitoring, employee training, and a commitment to data security best practices are essential for safeguarding this valuable information. The cost of inaction far outweighs the investment in preventative measures. Embrace a culture of security, and make PII protection a top priority. Remember, the consequences of a data breach can be severe and far-reaching. Proactive and comprehensive strategies are crucial for mitigating risks and safeguarding personal information effectively.
Latest Posts
Latest Posts
-
Which Of The Following Describes The Event Of Ovulation
Mar 25, 2025
-
Documentation Of Training Education And Qualification Completion Is Maintained
Mar 25, 2025
-
Aetna Medicare Dsnp Has Expanded Into This State In 2024
Mar 25, 2025
-
Explain How Idealogical Orientation Influenced Voters Choice In An Election
Mar 25, 2025
-
In A Resting State Sodium Is At A Higher Concentration
Mar 25, 2025
Related Post
Thank you for visiting our website which covers about Identifying And Safeguarding Personally Identifiable Information Quizlet . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
