What Statement Describes A Characteristic Of Mac Addresses
Breaking News Today
Mar 28, 2025 · 5 min read
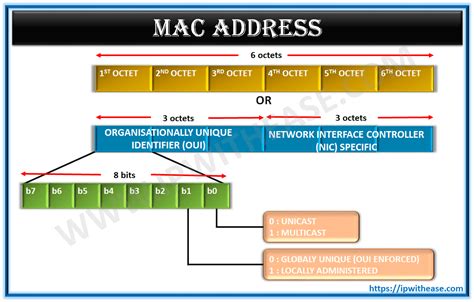
Table of Contents
What Statement Describes a Characteristic of MAC Addresses?
Media Access Control (MAC) addresses are unique identifiers assigned to network interfaces for communication on a network. Understanding their characteristics is crucial for network administration, troubleshooting, and security. This comprehensive guide delves into the defining characteristics of MAC addresses, exploring their structure, functionality, and implications for network management.
The Uniqueness of MAC Addresses: A Defining Characteristic
Perhaps the most critical characteristic of a MAC address is its uniqueness. No two devices manufactured globally should possess the same MAC address. This uniqueness is paramount for several reasons:
-
Network Identification: MAC addresses allow network devices to identify each other unequivocally. This is essential for routing data packets to the correct destination. Without unique identifiers, network communication would descend into chaos.
-
Security Implications: The uniqueness of MAC addresses plays a vital role in network security. Access control lists (ACLs) and other security measures can utilize MAC addresses to filter network traffic, preventing unauthorized access to sensitive data or network resources.
-
Troubleshooting and Diagnostics: When network problems arise, the unique MAC address helps pinpoint the malfunctioning device. Network administrators can quickly isolate the source of the issue, enhancing the efficiency of troubleshooting procedures.
-
Device Tracking and Management: Network monitoring tools utilize MAC addresses to track device activity and location within the network. This capability is invaluable for network management and security audits.
MAC Address Structure: Understanding the Components
A MAC address is a 48-bit (6-byte) hexadecimal number, typically represented as six groups of two hexadecimal digits separated by colons (e.g., 00:16:3E:00:00:01). Let's break down the structure:
-
Organizationally Unique Identifier (OUI): The first three bytes (24 bits) of a MAC address represent the OUI. This portion is assigned by the IEEE (Institute of Electrical and Electronics Engineers) to network interface card (NIC) manufacturers. It identifies the vendor that produced the network interface.
-
Device Identifier: The remaining three bytes (24 bits) are the device identifier. This part is unique to a specific NIC within a manufacturer's product line. The manufacturer uses this to distinguish individual devices they produce.
This hierarchical structure guarantees the uniqueness of each MAC address, even with massive global device deployment.
Other Key Characteristics of MAC Addresses
Beyond uniqueness, several other characteristics define MAC addresses:
1. Physical Layer Addressing: A Hardware-Level Identifier
MAC addresses reside at the data link layer (Layer 2) of the OSI model. Unlike IP addresses which are logical addresses assigned to devices within a network, MAC addresses are physically embedded in the network interface hardware. This means the MAC address is hard-coded into the NIC itself, making it a hardware-level identifier. Changing a MAC address typically requires physically modifying the NIC's hardware or using software spoofing (which is often against network policy).
2. Locally Administered Addresses: Flexibility for Virtualization and Internal Networks
MAC addresses are generally categorized into two types: universally administered addresses and locally administered addresses. Universally administered addresses are assigned by the IEEE and are permanently linked to the NIC hardware. However, locally administered addresses offer greater flexibility. These addresses are assigned by the network administrator and are typically used in situations such as:
-
Virtual Machines: Virtual machines (VMs) often employ locally administered MAC addresses to prevent address conflicts with physical network devices.
-
Internal Networks: Locally administered addresses can be helpful in internal testing networks or environments where strict IEEE address allocation isn't necessary.
-
Network Device Emulation: In network simulation and testing environments, locally administered MAC addresses can be used to emulate various network devices.
It's crucial to understand the implications of using locally administered addresses, particularly regarding network security and interoperability with external networks.
3. Static vs. Dynamic Assignment: A Matter of Configuration
While MAC addresses are inherently assigned at the hardware level, their association with specific IP addresses can be static or dynamic.
-
Static MAC Address Assignment: In this scenario, the MAC address is directly mapped to a specific IP address using network configuration. This is often used for servers or devices requiring consistent network connectivity.
-
Dynamic MAC Address Assignment: This setup involves utilizing DHCP (Dynamic Host Configuration Protocol), which dynamically assigns IP addresses based on available network resources. While the MAC address remains constant, the IP address assigned to the device may change. This is common for client devices in typical home and office networks.
The choice between static and dynamic assignment depends on the device's role and network configuration requirements.
MAC Address Spoofing: A Security Concern
MAC address spoofing is a technique where a device's MAC address is altered to mimic another device's address. This practice can be used for malicious purposes, such as:
-
Network Intrusion: An attacker could spoof a legitimate device's MAC address to gain unauthorized access to the network.
-
Evasion of Access Controls: If a network uses MAC address filtering for security, spoofing can circumvent these measures.
-
Denial-of-Service Attacks: Spoofing can be used in conjunction with other attacks to disrupt network services.
While MAC address spoofing is technically possible, most modern networks implement security mechanisms to detect and mitigate this threat. Network administrators should employ strong security practices to prevent MAC address spoofing and related attacks.
Practical Applications and Implications
Understanding MAC address characteristics is crucial for various applications, including:
-
Network Security Audits: Analyzing MAC address activity can help identify potential security breaches or unauthorized network access.
-
Troubleshooting Network Connectivity Issues: Identifying devices using their MAC addresses is a vital step in diagnosing and resolving network connectivity problems.
-
Wireless Network Management: Wireless access points often use MAC address filtering to control which devices can connect to the network.
-
Network Inventory Management: Tracking MAC addresses provides a comprehensive inventory of all devices connected to the network.
-
Forensic Investigations: In cases of cybercrime, analyzing MAC address data can provide valuable evidence for investigators.
Conclusion: MAC Addresses - The Foundation of Network Identification
MAC addresses are fundamental to network communication and management. Their inherent uniqueness, physical layer addressing, and flexibility in assignment contribute to their critical role in various network applications. Understanding their characteristics – from their structure and assignment to the security implications of spoofing – is essential for network administrators, security professionals, and anyone involved in managing or troubleshooting network infrastructure. This knowledge empowers effective network management, strengthens security posture, and facilitates efficient problem-solving in complex network environments. The continuing evolution of networking technologies reinforces the enduring importance of MAC addresses in the world of network communication.
Latest Posts
Latest Posts
-
Anatomy And Physiology 2 Exam 1 Quizlet
Mar 31, 2025
-
Fluid Electrolyte And Acid Base Balance Ati Quizlet
Mar 31, 2025
-
Functionalist Psychologists Focus On The Function Of Behavior And
Mar 31, 2025
-
Functions Of The Large Intestine Include Quizlet
Mar 31, 2025
-
An Interval Of An Ecg Is Quizlet
Mar 31, 2025
Related Post
Thank you for visiting our website which covers about What Statement Describes A Characteristic Of Mac Addresses . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
