Your Coworker Was Teleworking When The Agency
Breaking News Today
Mar 19, 2025 · 6 min read
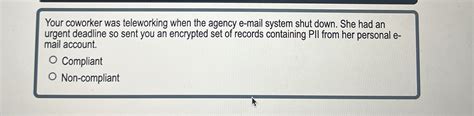
Table of Contents
Your Coworker Was Teleworking When the Agency…
The flickering fluorescent lights of the office felt oddly silent. Usually, a cacophony of ringing phones, keyboard clicks, and murmured conversations filled the air. Today, only the hum of the air conditioning competed with the frantic drumming of my fingers on my desk. The news had broken just an hour ago: a major security breach at our agency. And Mark, my coworker, the one who'd been diligently teleworking all week, was nowhere to be found. The situation was escalating quickly, turning a routine Tuesday into a full-blown crisis.
The Initial Shock and Scramble
The initial reaction was pure chaos. Emails flew back and forth, a frantic symphony of questions and half-answers. Our manager, Sarah, a woman usually known for her calm demeanor, was visibly stressed. The breach, it seemed, had compromised sensitive client data, potentially exposing confidential information to malicious actors. The severity was staggering.
The immediate priority was damage control. We were instructed to disconnect from the network, change all passwords, and prepare for a full-scale audit. But a nagging question persisted in the back of my mind: where was Mark? He was the one responsible for maintaining the server's security protocols. He'd been working remotely all week, ostensibly to avoid the usual office distractions. Now, that isolation felt less like a productivity boost and more like a potential disaster.
The Search Begins
Sarah initiated a company-wide search. Emails were sent, calls were made, but there was no response from Mark. His phone went straight to voicemail, and his usual online presence was absent. The situation became increasingly desperate. The longer we couldn't reach him, the greater the fear that the breach was somehow connected to his remote setup. Had his home network been compromised? Was he a victim of a targeted attack? Or worse, was he involved?
Unraveling the Mystery
The next few hours were a blur of frantic activity. IT specialists were called in to investigate the extent of the breach. Law enforcement was notified. Meanwhile, a small team, including myself, was tasked with piecing together Mark's recent activities. We reviewed his work logs, his email correspondence, and his access records. We scoured his project files, looking for any clues that could explain his sudden disappearance.
The more we investigated, the more unsettling the picture became. His recent work involved a particularly sensitive client, a major pharmaceutical company with highly confidential research data. There were unusual access patterns in his logs, showing late-night activity from an unfamiliar IP address. And most alarmingly, there was a large file transfer, seemingly uploaded to an unknown external server, just hours before the breach was detected.
The Suspicion Mounts
The growing evidence pointed towards a potential insider threat. While it was initially difficult to accept, the possibility that Mark was somehow involved became increasingly hard to ignore. Had he been compromised? Or was he a willing participant in the breach? The thought was unsettling, the idea that someone we worked with, someone we trusted, could betray the agency in such a significant way, was almost unbearable.
We examined Mark's personal history, searching for any signs of financial difficulties, personal conflicts, or resentment towards the agency. Nothing concrete emerged, but the lack of a clear motive only deepened the mystery and the uncertainty.
The Breakthrough
Days turned into weeks. The investigation continued relentlessly. The IT team finally managed to trace the suspicious file transfer to a dark web server known for hosting stolen data. But there was more. They also discovered a hidden backdoor in the agency’s system, expertly concealed and almost impossible to detect. This backdoor allowed unauthorized access to the server, providing a clear path for the data breach.
The breakthrough came unexpectedly. A seemingly insignificant detail within Mark’s work log – a specific software package he had accessed – piqued the interest of one of the investigators. It turned out that this software was known to be used for creating and managing encrypted communication channels, often employed by hackers and malicious actors.
Further investigation revealed that Mark had used this software to communicate with a known cybercrime syndicate, exchanging files and information related to the agency's security systems. The evidence was undeniable. Mark had not been a victim; he was the perpetrator.
The Aftermath
The revelation sent shockwaves through the agency. The emotional toll on everyone involved was significant. Trust had been shattered, and the sense of betrayal was palpable. Beyond the immediate crisis management, the agency faced a long road to recovery. Rebuilding trust, strengthening security protocols, and managing the legal and reputational consequences of the breach demanded extensive effort. The damage extended far beyond the mere loss of data.
Lessons Learned: Preventing Future Breaches
This incident served as a harsh but crucial lesson. The incident highlighted the vulnerabilities of remote work environments and underscored the importance of comprehensive security protocols, rigorous employee background checks, and advanced threat detection systems. It was a wake-up call to all organizations, not just ours.
Here's a breakdown of key lessons learned:
- Enhanced Security Protocols: We implemented multi-factor authentication, advanced intrusion detection systems, and regular security audits.
- Employee Vetting: More stringent background checks and psychological assessments were introduced for all employees, especially those handling sensitive information.
- Security Awareness Training: Regular, comprehensive training programs were developed to educate employees about phishing scams, malware, and other cyber threats.
- Remote Work Security Guidelines: Detailed guidelines for secure remote work practices were created, encompassing VPN usage, secure Wi-Fi networks, and endpoint protection.
- Incident Response Plan: A comprehensive incident response plan was developed to ensure a swift and coordinated response to future security breaches.
The Importance of Trust and Collaboration
The experience reinforced the crucial role of trust and collaboration within an organization. While the betrayal by Mark deeply affected the morale, it also brought the team closer. We learned to rely on each other, supporting one another during the challenging time. The collective effort to investigate the breach, recover from its impact, and implement improved security measures ultimately strengthened our team and made us more resilient.
The experience, though painful, taught us valuable lessons about vigilance, cybersecurity, and the human element in security. It served as a stark reminder that even within the seemingly secure confines of an established institution, threats can arise from unexpected sources. It underscored the importance of constant vigilance, robust security measures, and the enduring power of trust and collaboration in navigating the complex landscape of cybersecurity. Ultimately, this incident became a catalyst for positive change, pushing us to adapt, improve, and prepare for the future challenges of the digital world. The silence in the office that day was replaced with the determined hum of collective effort, the commitment to learn, adapt, and never let a similar situation happen again.
Latest Posts
Latest Posts
-
Economic Cost Can Best Be Defined As
Mar 19, 2025
-
The Food Code Is Created By Which Government Agency
Mar 19, 2025
-
4 Ways Physical Characteristics Of A Fiber Can Be Examined
Mar 19, 2025
-
Entrepreneurs Who Want To Open A Franchise
Mar 19, 2025
-
Which Group Of Mollusks Are Highly Endangered In The Us
Mar 19, 2025
Related Post
Thank you for visiting our website which covers about Your Coworker Was Teleworking When The Agency . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
