Which Of The Following Is Associated With Port Security
Breaking News Today
Mar 22, 2025 · 6 min read
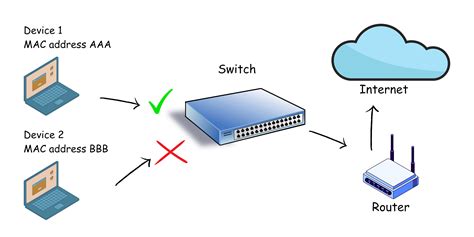
Table of Contents
Which of the following is associated with port security? A Deep Dive into Network Security
Port security, a critical component of network security, focuses on protecting network ports from unauthorized access and malicious activities. Understanding what constitutes port security is crucial for maintaining a robust and secure network infrastructure. This article will delve deep into the various aspects associated with port security, exploring its key features, methodologies, and best practices.
Understanding Port Security: More Than Just Access Control
Port security is far more comprehensive than simply restricting access. It encompasses a multi-layered approach designed to mitigate risks associated with unauthorized connections, rogue devices, and malicious attacks targeting network ports. Think of it as a sophisticated gatekeeper, meticulously vetting each connection attempt before granting access. Its importance cannot be overstated in today's interconnected world, where vulnerabilities can quickly lead to devastating breaches.
Key Aspects Associated with Port Security
Several key features and functionalities are inherently associated with effective port security implementations:
-
MAC Address Filtering: This is a fundamental aspect of port security. It involves creating a whitelist of authorized MAC addresses. Only devices with MAC addresses on this list are permitted to connect to the port. This prevents unauthorized devices from gaining access. Implementing robust MAC address filtering is a critical first step in bolstering port security.
-
Port Security Protocols: Various protocols enhance port security capabilities. These include:
- 802.1X Authentication: This standard provides a robust method for authenticating devices before granting network access. It often involves using a RADIUS server to verify user credentials and assign appropriate network privileges. 802.1X is considered a best practice for securing network ports, especially in sensitive environments.
- Dynamic Access Control Lists (ACLs): ACLs dynamically adjust network access based on pre-defined rules and real-time network conditions. They can be configured to block or permit traffic based on various criteria, enhancing flexibility and responsiveness in managing port access. Dynamic ACLs are particularly useful in dynamic environments where devices connect and disconnect frequently.
- Network Access Control (NAC): NAC solutions go beyond simple authentication, performing health checks and ensuring devices meet security requirements before granting access. This proactive approach helps prevent infected devices from compromising the network. NAC significantly strengthens port security by preventing compromised devices from joining the network.
-
Port Security Limits: Restricting the number of active connections per port helps prevent denial-of-service (DoS) attacks that could overwhelm a port with excessive requests. By limiting the number of MAC addresses associated with a port, organizations prevent unauthorized devices from saturating network resources. Setting appropriate port security limits is essential to protect against DoS attacks and resource exhaustion.
-
Port Security Logging and Monitoring: Comprehensive logging provides invaluable insight into port activity. This enables administrators to track connections, identify suspicious behavior, and react quickly to potential security threats. Regular monitoring and analysis of port security logs are crucial for maintaining a secure network. Effective logging and monitoring are essential for proactive security management and incident response.
-
Security Hardening: Beyond specific port security features, the overall security posture of the network plays a significant role. This includes regular software updates, strong password policies, intrusion detection systems, and firewalls. Addressing security holistically is critical to maximizing the effectiveness of port security measures.
Implementing Effective Port Security: A Step-by-Step Guide
Implementing robust port security requires a methodical approach. The following steps outline a comprehensive strategy:
-
Network Assessment: Begin by conducting a thorough assessment of your network infrastructure. Identify critical ports, assess existing security measures, and determine potential vulnerabilities. This provides a baseline for planning and implementation.
-
Define Security Policies: Develop clear and comprehensive security policies that outline acceptable use, access control, and incident response procedures. These policies should be well-documented and communicated to all users.
-
Choose Appropriate Port Security Technologies: Select the most suitable technologies based on your network infrastructure, budget, and security requirements. Consider a combination of techniques such as MAC address filtering, 802.1X authentication, and ACLs.
-
Configure Port Security Settings: Carefully configure your chosen technologies, ensuring accurate and robust settings. Test the configurations thoroughly before deploying them in a production environment.
-
Monitor and Log Port Activity: Implement robust logging and monitoring to track port activity, identify suspicious behavior, and react quickly to potential threats. Regularly review logs to identify trends and adjust security measures as needed.
-
Regular Security Audits: Conduct regular security audits to assess the effectiveness of your port security measures. Identify any weaknesses or vulnerabilities and address them promptly.
Advanced Port Security Techniques: Going Beyond the Basics
For advanced security needs, consider the following techniques:
-
Guest VLANs: Separate guest traffic from the main network using VLANs. This isolates guest devices and minimizes the risk of compromise.
-
Role-Based Access Control (RBAC): Implement RBAC to granularly control access based on user roles and responsibilities. This provides a more flexible and efficient way to manage access permissions.
-
Security Information and Event Management (SIEM): Integrate port security logs with a SIEM system to gain comprehensive visibility across the entire network. SIEM systems provide advanced analytics and threat detection capabilities.
-
Network Segmentation: Divide the network into smaller, isolated segments to limit the impact of security breaches. This approach helps contain attacks and prevent them from spreading throughout the network.
Addressing Common Challenges in Port Security Implementation
Implementing effective port security can present various challenges:
-
Complexity: Managing and configuring port security can be complex, especially in large networks.
-
Cost: Implementing advanced port security solutions can be expensive, requiring significant investment in hardware and software.
-
Maintenance: Maintaining and updating port security configurations requires ongoing effort and expertise.
-
Integration: Integrating port security solutions with existing network infrastructure can be challenging.
Best Practices for Maintaining Robust Port Security
-
Regularly Update Software and Firmware: Keep your network devices updated with the latest security patches and firmware to address known vulnerabilities.
-
Strong Password Policies: Enforce strong password policies to prevent unauthorized access.
-
Principle of Least Privilege: Grant users only the minimum necessary access privileges.
-
Regular Security Audits and Penetration Testing: Regularly audit your security posture and conduct penetration testing to identify weaknesses.
-
Employee Training: Educate employees about security best practices and potential threats.
Conclusion: Proactive Port Security for a Secure Network
Port security is a fundamental aspect of overall network security. By implementing robust port security measures and following best practices, organizations can significantly reduce their risk of security breaches and maintain a secure and reliable network infrastructure. The techniques and strategies discussed in this article provide a comprehensive guide to establishing a proactive and robust port security posture, ultimately protecting valuable data and resources from unauthorized access and malicious attacks. Remember that a layered security approach, incorporating multiple layers of defense, is always the most effective strategy. Consistent monitoring, vigilant updates, and proactive security practices are vital for maintaining a strong and resilient network against ever-evolving threats.
Latest Posts
Latest Posts
-
What Is The Function Of The Auditory Tube Quizlet
Mar 23, 2025
-
What Is The Functional Role Of The T Tubules Quizlet
Mar 23, 2025
-
Fluid Electrolyte And Acid Base Regulation Ati Quizlet
Mar 23, 2025
-
Which Is A Source Of Land Pollution Quizlet
Mar 23, 2025
-
Acetylcholine Is Released From A Neuron Quizlet
Mar 23, 2025
Related Post
Thank you for visiting our website which covers about Which Of The Following Is Associated With Port Security . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.
